Security, confidentiality, and privacy are essential components of information systems, ensuring the protection of sensitive data from unauthorized access, misuse, or breaches. These concepts help maintain trust, regulatory compliance, and operational integrity. Security focuses on safeguarding systems, confidentiality ensures data access is restricted to authorized users, and privacy governs the ethical handling of personal information. Organizations use frameworks like COBIT and NIST, along with tools such as encryption and multi-factor authentication, to manage risks, prevent data loss, and respond to cyber threats effectively.
Learning Objectives
In studying “Security, Confidentiality, and Privacy” for the CPA Exam, you should learn to understand key principles like the CIA Triad (Confidentiality, Integrity, Availability) and how they apply to information systems. Analyze frameworks such as COBIT and NIST, focusing on security technologies like encryption, firewalls, and multi-factor authentication. Evaluate privacy regulations like GDPR, HIPAA, and CCPA to ensure compliance. Explore incident response planning, access controls, and data loss prevention (DLP) tools, and how these practices protect sensitive information. Apply your knowledge by interpreting case-based scenarios involving internal controls, risk management, and audit processes related to IT systems in CPA practice.
1. Information Security Principles and Frameworks
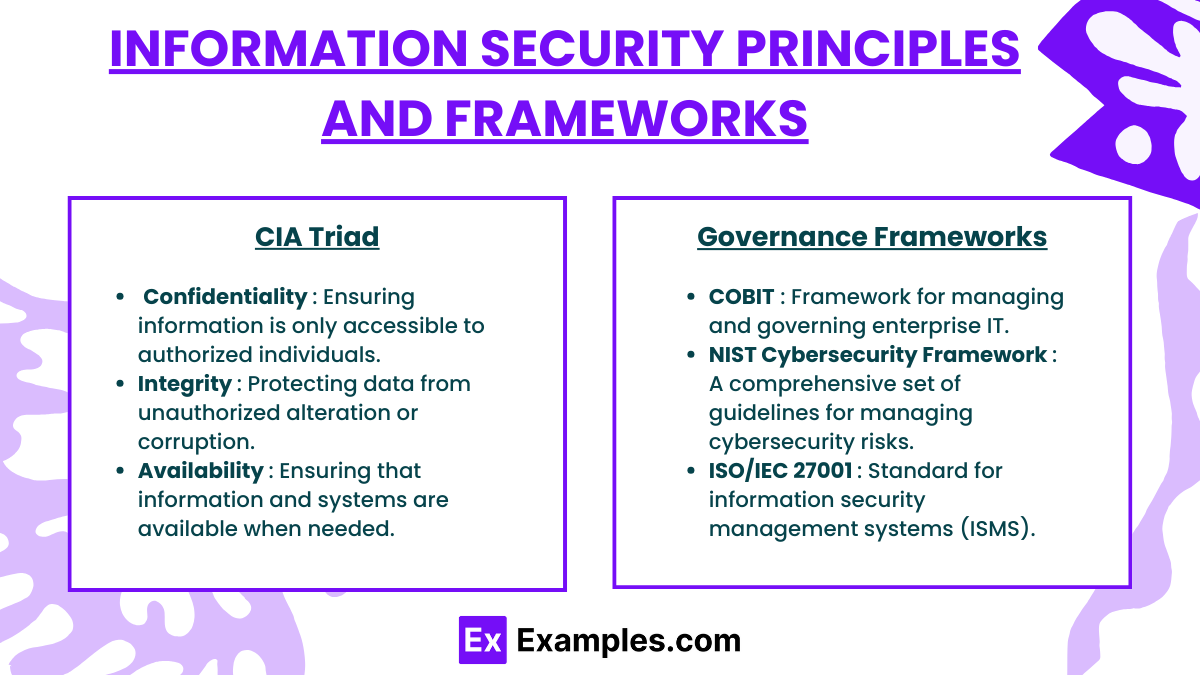
- CIA Triad: The core principles of information security:
- Confidentiality: Ensuring information is only accessible to authorized individuals.
- Integrity: Protecting data from unauthorized alteration or corruption.
- Availability: Ensuring that information and systems are available when needed.
- Governance Frameworks:
- COBIT (Control Objectives for Information and Related Technologies): Framework for managing and governing enterprise IT.
- NIST Cybersecurity Framework: A comprehensive set of guidelines for managing cybersecurity risks.
- ISO/IEC 27001: Standard for information security management systems (ISMS).
2. Confidentiality: Protection of Sensitive Information

- Definition: Confidentiality involves ensuring that sensitive information (such as financial data or personal information) is only accessible to those authorized to view it.
- Access Controls:
- Role-Based Access Control (RBAC): Users can only access data relevant to their job roles.
- Least Privilege Principle: Users are granted the minimum access necessary for their tasks.
- Multi-Factor Authentication (MFA): Adds layers of security beyond passwords.
- Encryption:
- Data at Rest: Protecting stored data with encryption.
- Data in Transit: Securing data transmitted across networks.
- Data Masking and Anonymization:
- Masking involves obscuring data (e.g., showing only the last four digits of a credit card).
- Anonymization removes personal identifiers to protect individual privacy.
3. Privacy Regulations and Compliance
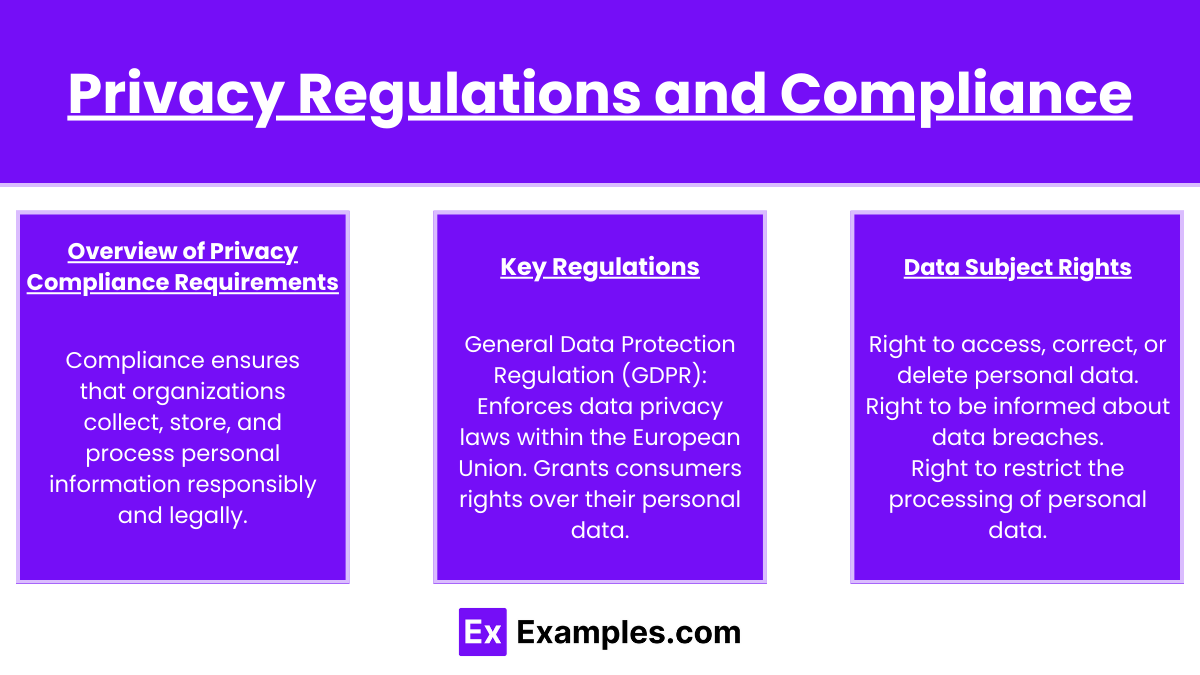
- Overview of Privacy Compliance Requirements:
- Compliance ensures that organizations collect, store, and process personal information responsibly and legally.
- Key Regulations:
- General Data Protection Regulation (GDPR): Enforces data privacy laws within the European Union.
- California Consumer Privacy Act (CCPA): Grants consumers rights over their personal data.
- Health Insurance Portability and Accountability Act (HIPAA): Protects sensitive patient information in healthcare.
- Data Subject Rights:
- Right to access, correct, or delete personal data.
- Right to be informed about data breaches.
- Right to restrict the processing of personal data.
4. Security Technologies and Threat Mitigation
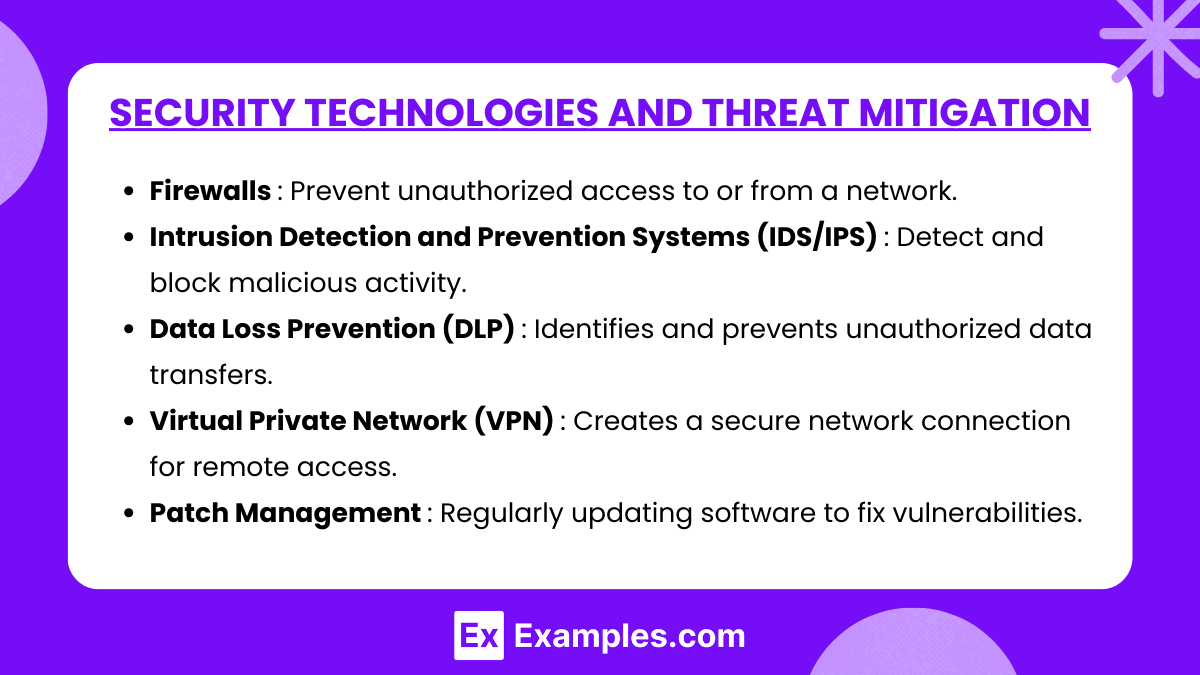
- Firewalls: Prevent unauthorized access to or from a network.
- Intrusion Detection and Prevention Systems (IDS/IPS): Detect and block malicious activity.
- Data Loss Prevention (DLP): Identifies and prevents unauthorized data transfers.
- Virtual Private Network (VPN): Creates a secure network connection for remote access.
- Threat Mitigation Strategies:
- Patch Management: Regularly updating software to fix vulnerabilities.
- Anti-Malware Tools: Detecting and removing malicious software.
- User Training: Educating employees to avoid phishing and social engineering attacks.
Examples
Example 1: Encryption of Financial Data During Transmission and Storage
Organizations use encryption to secure sensitive financial information such as client details, credit card numbers, and payroll data. Encryption ensures that even if hackers intercept the data, it remains unreadable without the decryption key. For CPAs, this is critical when auditing organizations that handle large volumes of personal or financial data, ensuring compliance with data protection laws like GDPR and CCPA.
Example 2: Role-Based Access Control (RBAC) for Accounting Systems
CPAs must ensure that only authorized individuals have access to specific parts of the accounting system. For instance, entry-level employees might access only accounts payable records, while senior accountants can view the general ledger. Implementing RBAC protects confidential financial data by limiting access based on job roles, aligning with the principle of least privilege to minimize internal security risks.
Example 3: Data Loss Prevention (DLP) Tools to Prevent Unauthorized Transfers
DLP systems monitor data flow to prevent sensitive information from leaving the organization through unauthorized channels. CPAs may evaluate the effectiveness of DLP tools during audits to ensure compliance with internal controls and regulatory requirements. These tools can prevent the accidental or deliberate sharing of confidential financial reports or client information, maintaining data privacy and organizational reputation.
Example 4: Incident Response Plan (IRP) for Financial Systems Breaches
An IRP outlines procedures for handling cybersecurity incidents, such as ransomware attacks targeting financial records. A well-prepared organization can minimize downtime, reduce financial losses, and protect sensitive data from exposure. CPAs evaluate the adequacy of IRPs and verify whether organizations conduct regular tests of these plans to ensure swift recovery from security incidents.
Example 5: Auditing Cloud Storage Solutions for Confidentiality Compliance
As many organizations store data in the cloud, CPAs must assess the security measures employed by cloud service providers. This includes ensuring encryption, multi-factor authentication, and proper user access controls are in place. CPAs also verify that service providers comply with privacy regulations and contractual obligations, reducing risks related to data breaches or unauthorized data access.
Practice Questions
Question 1
Which of the following principles best ensures that sensitive data is protected from unauthorized access?
A) Availability
B) Integrity
C) Confidentiality
D) Authorization
Answer: C) Confidentiality
Explanation: Confidentiality ensures that sensitive information is accessible only to authorized individuals and protected from unauthorized access or disclosure. Measures to maintain confidentiality include encryption, access controls, and data masking. This principle is vital for organizations handling financial records and personal data, ensuring compliance with privacy regulations like GDPR or CCPA. Availability and integrity are important security principles but do not directly address restricting access to sensitive data. Authorization refers to the process of granting access but is part of maintaining confidentiality.
Question 2
Which of the following is an example of the least privilege principle in action?
A) A junior accountant has unrestricted access to all financial reports.
B) A payroll specialist can only access payroll processing software.
C) A company grants employees access to all systems during onboarding.
D) Employees use shared passwords for critical systems to ensure faster access.
Answer: B) A payroll specialist can only access payroll processing software.
Explanation: The least privilege principle ensures that users are granted only the minimum level of access necessary to perform their tasks. This reduces the risk of internal security breaches and limits the exposure of sensitive information. In this case, the payroll specialist is restricted to only the software relevant to payroll processing, aligning with this principle. Option A violates this principle by giving excessive access, and options C and D introduce risks by over-permitting access or sharing credentials, which is a security concern.
Question 3
What is the primary purpose of an Incident Response Plan (IRP) in information systems?
A) To define roles for monitoring financial transactions.
B) To ensure financial reports are generated accurately.
C) To outline procedures for managing security breaches and incidents.
D) To maintain compliance with tax filing deadlines.
Answer: C) To outline procedures for managing security breaches and incidents.
Explanation: An Incident Response Plan (IRP) is a structured approach to detecting, responding to, and recovering from security breaches. It defines the roles and responsibilities of personnel during incidents, details containment and recovery processes, and ensures lessons learned are applied to prevent future breaches. This plan ensures that organizations respond promptly to cybersecurity events, minimizing financial and reputational damage. Monitoring financial transactions and ensuring reporting accuracy are important tasks but are not the primary focus of an IRP.


