Safe computing is the practice of protecting personal data, digital devices, and networks from various security threats, such as viruses, malware, and unauthorized access. It involves using secure passwords, enabling two-factor authentication, maintaining up-to-date software, and practicing caution with suspicious emails or downloads. For AP Computer Science Principles, understanding safe computing is essential for recognizing potential risks and safeguarding sensitive information in a digital environment. By following best practices, users can minimize vulnerabilities and ensure data integrity, privacy, and secure communication in today’s interconnected world.
Learning Objectives
For the topic “Safe Computing” in AP Computer Science Principles, you should learn how to identify and implement security best practices for protecting personal and organizational data. This includes understanding encryption, secure data transmission, safe browsing habits, and protection against malware and social engineering attacks like phishing. Additionally, you should grasp legal and ethical considerations around data privacy, including regulations like GDPR. Understanding how to educate users about safe computing behaviors and the importance of regular software updates and backups is also essential.
Introduction to Safe Computing
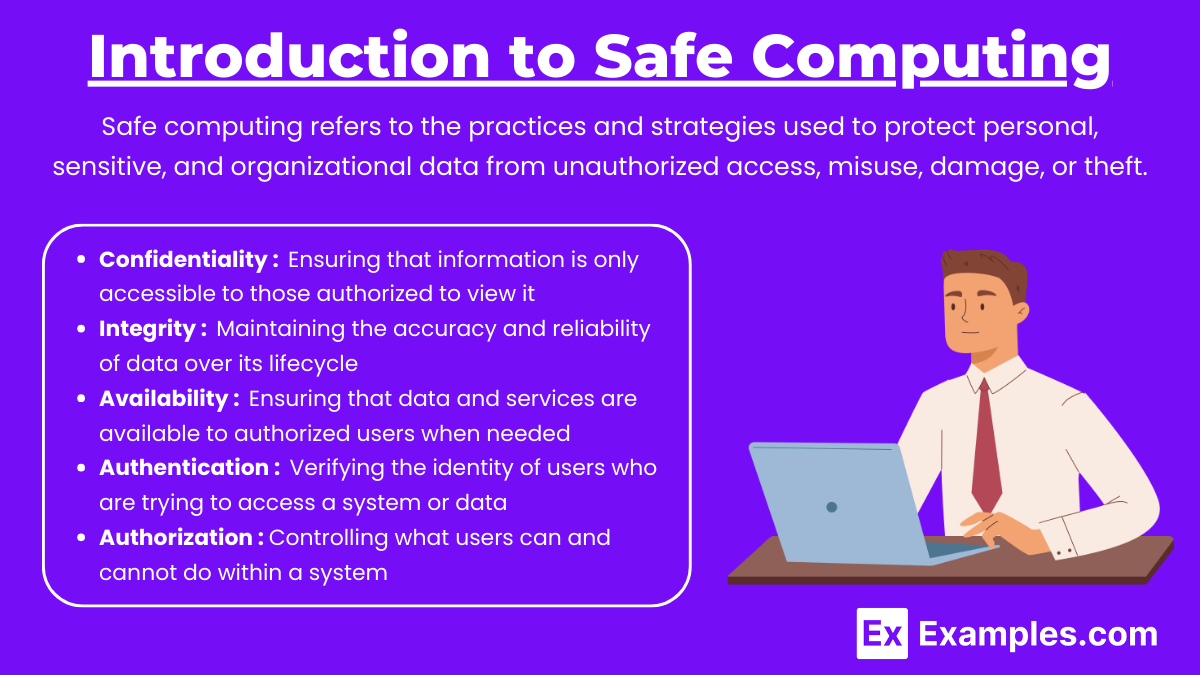
Safe computing refers to the practices and strategies used to protect personal, sensitive, and organizational data from unauthorized access, misuse, damage, or theft. With the increasing reliance on digital systems, ensuring cybersecurity and promoting ethical behavior in the use of technology are critical to maintain privacy and data integrity.
Key Concepts in Safe Computing:
- Confidentiality: Ensuring that information is only accessible to those authorized to view it. This is achieved through methods like encryption, passwords, and secure access controls.
- Integrity: Maintaining the accuracy and reliability of data over its lifecycle. Techniques like checksums, digital signatures, and hash functions help to verify data integrity.
- Availability: Ensuring that data and services are available to authorized users when needed. This includes protections against denial-of-service (DoS) attacks and implementing proper backup and recovery systems.
- Authentication: Verifying the identity of users who are trying to access a system or data. This is done using passwords, biometrics, or multi-factor authentication (MFA).
- Authorization: Controlling what users can and cannot do within a system. Users are granted specific rights and permissions to access certain data or perform certain tasks.
- Non-repudiation: Guaranteeing that an individual cannot deny having performed a particular action, such as sending a message. Digital signatures are used to ensure non-repudiation.
Threats to Safe Computing
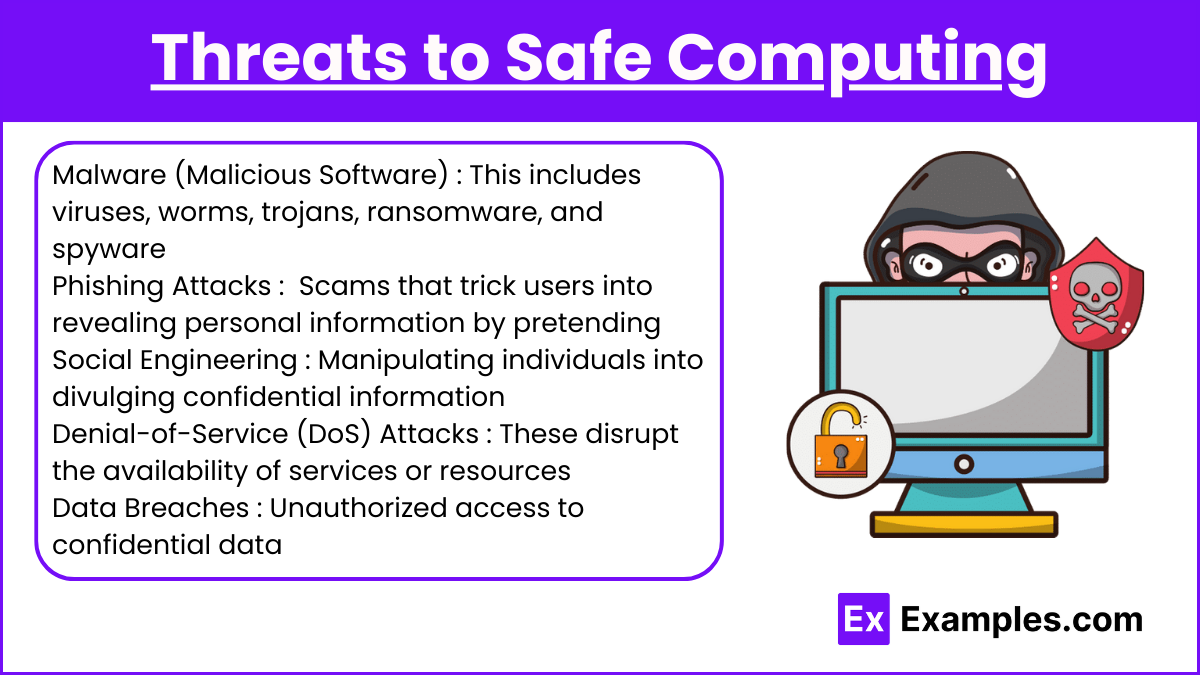
- Malware (Malicious Software): This includes viruses, worms, trojans, ransomware, and spyware that can harm computer systems or steal information.
- Phishing Attacks: Scams that trick users into revealing personal information by pretending to be a trustworthy entity.
- Social Engineering: Manipulating individuals into divulging confidential information. This can be done through emails, phone calls, or in person.
- Denial-of-Service (DoS) Attacks: These disrupt the availability of services or resources, making systems unusable for legitimate users.
- Data Breaches: Unauthorized access to confidential data, which can lead to identity theft, financial loss, and damage to reputations.
Best Practices for Safe Computing

- Strong Passwords: Use complex passwords that combine letters, numbers, and symbols. Avoid using easily guessable information such as birthdays or common words.
- Regular Software Updates: Keeping operating systems, browsers, and applications updated helps to patch security vulnerabilities.
- Antivirus Software: Install and maintain up-to-date antivirus and anti-malware software to detect and remove malicious threats.
- Firewalls: Use firewalls to monitor and control incoming and outgoing network traffic based on predetermined security rules.
- Secure Networks: Avoid using public Wi-Fi networks for sensitive activities. Use virtual private networks (VPNs) when accessing the internet over unsecured networks.
- Backup Data: Regularly back up important data to prevent loss from hardware failure, ransomware, or other disasters.
Ethical and Legal Considerations
Safe computing involves not only protecting data but also adhering to ethical and legal standards. Issues like intellectual property, data privacy (e.g., GDPR), and responsible use of technology fall under this category.
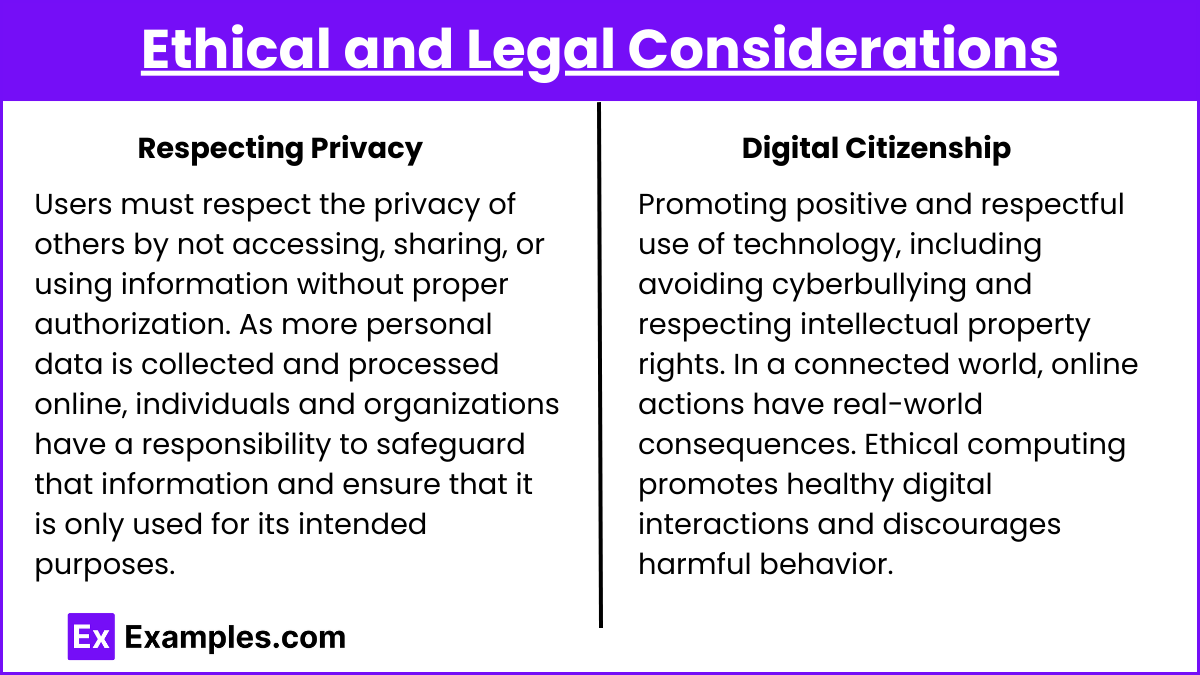
- Respecting Privacy: Users must respect the privacy of others by not accessing, sharing, or using information without proper authorization. As more personal data is collected and processed online, individuals and organizations have a responsibility to safeguard that information and ensure that it is only used for its intended purposes.
- Examples:
- Access Control: Users must not access or share information without proper authorization, as doing so can lead to privacy violations.
- Avoiding Surveillance: Unethical practices, such as unauthorized monitoring or tracking of individuals without their knowledge, are serious privacy violations and can result in legal consequences.
- Digital Citizenship: Promoting positive and respectful use of technology, including avoiding cyberbullying and respecting intellectual property rights. In a connected world, online actions have real-world consequences. Ethical computing promotes healthy digital interactions and discourages harmful behavior.
- Examples:
- Cyberbullying: One aspect of digital citizenship is avoiding harmful behaviors like cyberbullying, harassment, and defamation. Users must promote respectful communication in online forums and social media platforms.
- Digital Footprint: Users should be aware of their digital footprint—the trail of data left behind from online activities.
Examples
Example 1: Using Strong Passwords and Multi-Factor Authentication
One of the most fundamental practices of safe computing is the use of strong, unique passwords for each online account. A strong password typically includes a mix of uppercase and lowercase letters, numbers, and special characters. Multi-factor authentication (MFA), such as a text message code or authentication app, adds an extra layer of security, making it harder for unauthorized users to gain access to accounts even if a password is compromised.
Example 2: Keeping Software and Systems Updated
Regularly updating operating systems, applications, and security software is essential for safe computing. Updates often include patches for vulnerabilities that hackers might exploit. By keeping all software up to date, users minimize the chances of falling victim to cyber-attacks that target outdated systems. Automatic updates should be enabled to ensure patches are applied as soon as they are available.
Example 3: Being Cautious with Email Attachments and Links
A common way cybercriminals launch attacks is through email phishing scams, where they send emails that appear legitimate but contain malicious links or attachments. Practicing safe computing means never clicking on links or opening attachments from unknown or suspicious sources. Even if an email looks genuine, users should verify the sender’s identity before taking any action.
Example 4: Backing Up Data Regularly
Regular backups are a key aspect of safe computing. In the event of data loss due to malware, system failure, or accidental deletion, having a recent backup ensures that critical information can be restored quickly. Safe computing practices include storing backups in multiple locations, such as cloud storage and external drives, to protect against localized incidents like theft or physical damage.
Example 5: Using Encryption for Sensitive Data
Encrypting sensitive data, especially when it is being transmitted over the internet, is a crucial practice in safe computing. Encryption converts data into a secure code that unauthorized users cannot easily decipher. This is particularly important for financial transactions, personal communications, and storing confidential information. By using encryption protocols like HTTPS or VPNs, users ensure their data remains secure from eavesdropping or theft.
Multiple Choice Questions
Question 1
Which of the following practices is most effective in protecting personal information while using public Wi-Fi?
A) Using a firewall only
B) Enabling two-factor authentication (2FA)
C) Using a Virtual Private Network (VPN)
D) Frequently changing passwords
Answer: C) Using a Virtual Private Network (VPN)
Explanation: When using public Wi-Fi, your data is often more vulnerable to interception by malicious actors. A Virtual Private Network (VPN) encrypts your internet connection, making it difficult for anyone on the same public network to access your data. While enabling two-factor authentication (2FA) and frequently changing passwords are good security practices, they do not directly protect your connection on public Wi-Fi. A firewall helps but is not specifically designed to secure Wi-Fi connections like a VPN does.
Question 2
Which of the following best describes the purpose of encryption in safe computing?
A) To ensure software updates are automatically installed
B) To convert sensitive data into a format that can only be read by authorized users
C) To backup data automatically in case of a ransomware attack
D) To monitor internet traffic for potential threats
Answer: B) To convert sensitive data into a format that can only be read by authorized users
Explanation: Encryption transforms data into a coded format, which ensures that even if the data is intercepted or accessed by unauthorized users, it cannot be read without the proper decryption key. This is a fundamental practice in protecting sensitive information, especially when it is being transmitted over networks. The other options (automatic updates, backups, and traffic monitoring) are important for safe computing but are not the primary function of encryption.
Question 3
Which of the following is an example of a social engineering attack?
A) A virus that infects a system and deletes files
B) An unauthorized user gaining access to a network by guessing the password
C) A phishing email that tricks users into providing their login credentials
D) A DoS (Denial-of-Service) attack that floods a website with traffic
Answer: C) A phishing email that tricks users into providing their login credentials
Explanation: Phishing is a common type of social engineering attack where attackers use deceptive emails or messages to trick individuals into revealing sensitive information, such as login credentials or financial data. Social engineering relies on human interaction and manipulation, unlike technical attacks like viruses or denial-of-service (DoS) attacks. The other examples listed are technical in nature and do not involve the manipulation of human behavior, which is the key characteristic of social engineering.


