15+ Security Report Examples to Download
A Security Report is a crucial document that records and analyzes security incidents, risks, and vulnerabilities to ensure the safety of people, data, and assets. It provides detailed insights into security threats, preventive measures, and incident responses, helping businesses, organizations, and individuals make informed decisions. A well-structured security report includes key details such as the nature of the incident, its impact, and recommendations for future prevention. Whether for corporate security, cybersecurity, or physical safety, an effective security report enhances protection and ensures compliance with security standards.
What is Security Report?

Security Report Format
Title
Clearly state “Security Report” along with the date and organization name.
Introduction
Provide a brief overview of the report, including the purpose and scope.
Incident Details
Describe the security incident, including the date, time, location, and people involved.
Observations
Explain the key findings, potential risks, and vulnerabilities identified.
Actions Taken
Detail the immediate actions taken to handle the situation and mitigate risks.
Recommendations
Suggest preventive measures and security improvements to avoid similar incidents.
Conclusion
Summarize the key points and emphasize the importance of implementing security measures.
Appendix (If Needed)
Include supporting documents, images, or additional evidence related to the incident.
Security Report Example
Security Report Examples
Cyber Security Report

Information Security Report

Good Security Report

Software Security Report Template

Security Incident Report Template

Construction Security Incident Report Template

Mode and Security Audit Report
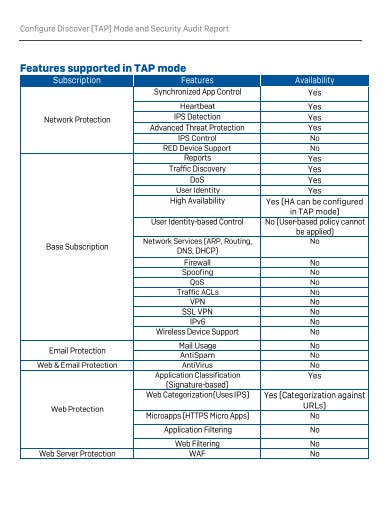
IT Security Audit Report Template

Security Assessment Report Form
Data Security Incident Response Report

Information Security Incident Report

Types of Security Report

1. Physical Security Report
This report documents incidents related to unauthorized access, theft, vandalism, or damage to physical assets. It includes details on security breaches, surveillance footage analysis, and preventive measures to enhance physical security.
2. Network Security Report
A network security report focuses on monitoring and assessing the security of an organization’s network infrastructure. It includes details on firewall breaches, unauthorized access attempts, malware detection, and recommendations for improving network defenses.
3. Data Breach Report
A data breach report provides an in-depth analysis of incidents where sensitive data has been exposed, leaked, or compromised. It details the source of the breach, the extent of data loss, affected individuals, and remediation actions taken to prevent further exposure.
4. Insider Threat Report
This report investigates security threats originating from within an organization, such as employees or contractors misusing their access privileges. It examines unauthorized data access, policy violations, and measures to mitigate insider threats.
5. Compliance Security Report
A compliance security report assesses whether an organization adheres to industry-specific security regulations and standards. It covers audits, risk assessments, and compliance gaps to ensure legal and regulatory requirements are met.
6. Security Audit Report
A security audit report provides a detailed evaluation of an organization’s security policies, procedures, and infrastructure. It highlights vulnerabilities, policy adherence, and recommended improvements for strengthening security frameworks.
7. Threat Intelligence Report
This report provides an analysis of emerging security threats and trends that could impact an organization. It includes intelligence gathered from various sources to predict and mitigate potential cyber or physical security risks.
8. Incident Response Report
An incident response report outlines the steps taken during and after a security incident. It includes detection, containment, eradication, and recovery efforts to restore normal operations and prevent future incidents.
9. Fraud Investigation Report
A fraud investigation report details cases of financial fraud, identity theft, or other deceptive activities within an organization. It includes evidence collection, investigative findings, and corrective actions to mitigate fraud risks.
10. Access Control Report
An access control report tracks and analyzes user access to restricted areas, digital systems, or confidential information. It helps in identifying unauthorized access attempts and improving authentication mechanisms.
How to Write a Security Report

Gather Accurate Information
Collect all relevant details, including the date, time, location, individuals involved, and specific security incident. Use firsthand accounts, surveillance footage, or system logs for accuracy.
Write a Clear Incident Description
Provide a detailed but concise account of what happened. Include what was observed, how the incident unfolded, and any security breaches or threats identified.
Include Evidence and Supporting Data
Attach relevant documents, images, logs, or witness statements to support your findings. Ensure all evidence is properly labeled and documented.
Provide Security Actions Taken
Explain the immediate and long-term actions taken to address the security issue. Detail how the threat was handled and any security measures implemented.
Make Recommendations for Prevention
Suggest improvements or security enhancements to prevent similar incidents in the future. Include policy changes, training recommendations, or technological upgrades needed.
How To Create a Security Report
- Identify the Purpose – Determine the objective of the report, whether it is to document an incident, assess vulnerabilities, or ensure compliance with security standards.
- Collect Essential Information – Gather details such as the date, time, location, individuals involved, nature of the incident, and any supporting evidence like surveillance footage or logs.
- Structure the Report Properly – Organize the report with clear sections, including an introduction, incident details, observations, actions taken, and recommendations for future security improvements.
- Use Clear and Concise Language – Write in a simple, factual, and professional manner. Avoid unnecessary jargon and ensure the report is easy to understand for all readers.
- Review and Finalize – Verify the accuracy of the information, check for any missing details, and ensure the report follows a logical flow. Proofread before submitting to ensure clarity and completeness.
FAQs
Why are Security Incident Reports important?
It is exceptionally imperative to report incidents to the company’s security group to examine the conceivable dangers of the occurrence. Such reports are dependable for setting up security arrangements and conventions for the organization.
What is an example of an incident?
An incident is something conceivable as a result of something else. A case of occurrence is somebody being put to prison after being caught for shoplifting.
What are the three types of security?
There are three essential areas or classifications of security controls. These are, incorporate administration security, operational security, and physical security controls.


