5+ Security Gap Analysis Examples to Download
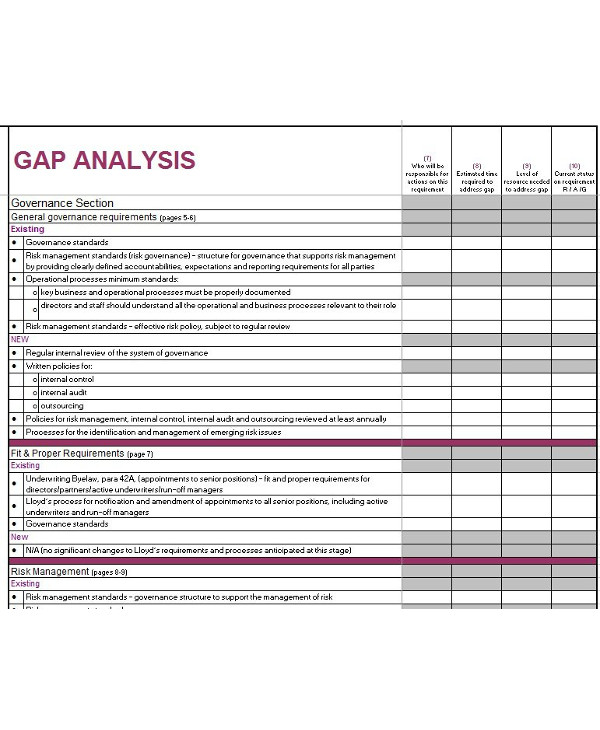
The Information Security Gap Analysis is a tool designed to assist your organization in obtaining full compliance with the appropriate regulations, guidelines, and best practice standards. The resulting report will be the summary of your organization’s current level of compliance and provide the details for developing appropriate corrective action.
The gap analysis is composed of a series of questions for each section and seeks to discover if there is a documented process in place that can adequately address the intent of each requirement. The questions will be answered and will include justification for each response. The identified gaps will provide the management with a deeper insight into the areas within the information security program that needs to be improved.You may also see quantitative risk analysis examples.
SASecurity Gap Analysis Example

The gap analysis process will involve determining, documenting, and obtaining the management’s recognition of the differences between the requirements set by regulation and the organization’s current information security program. Once the gaps are identified, a security improvement plan can be developed to provide a foundation for setting priorities; assigning ownership; allocating investments of time, money, and human resources; and for measuring and improving compliance with the guidelines.
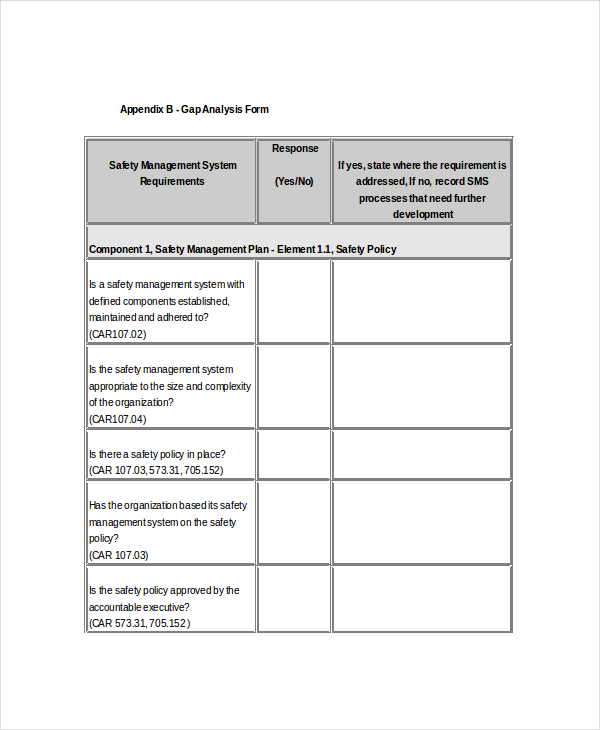
Security Safety Gap Analysis Form
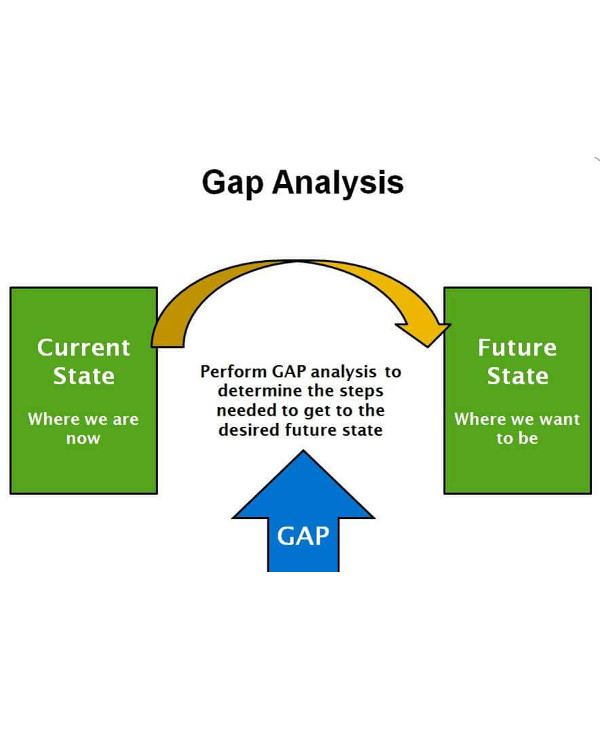
Security Gap Analysis Cycle
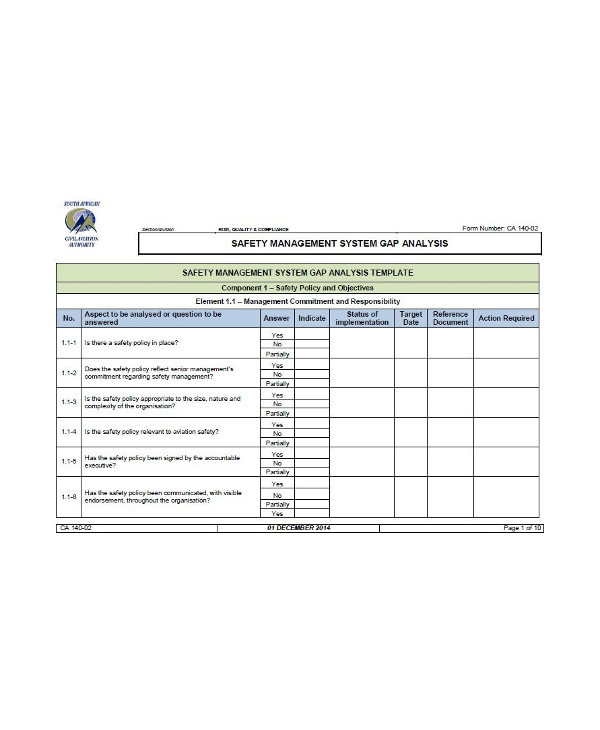
Safety Management System Gap Analysis
Security Gap Analyses
Contrary to popular opinion, information security shouldn’t just be an IT issue. Many people forget that organizations nowadays rely heavily on technology for their business operations. Gone are the days when files were stored in cabinets, and everything was handwritten. Now, computers play just as important roles as manpower.You may also see job safety analysis examples.
Aside from this undeniable fact, internet threats are also appearing with unprecedented speed and complexity, which means that business assets are being put to increased risk. This new dilemma has opened the government to enforce industry regulations that challenge businesses to meet a range of very strict requirements for information security.You may also see bowtie risk analysis examples.
Simply by knowing these two reasons, companies are forced to heighten their information security in order to keep their data away from the hands of people who may mistreat it. After all, it’s all about confidentiality, integrity, and availability. Programs must protect the sensitive information that they hold from unauthorized disclosure or access. You may also see activity analysis examples.
It is now every business’s priority to make sure that the integrity of their information is not compromised, and that it will always remain accessible only by authorized individuals who may use it whenever, wherever, and however they need it.You may also see Job task analysis examples.
As a result, many businesses are devoting a bigger part of their time and resources to develop a formal, structured information security program that will help ensure the security of their business assets and operations in the form of computer data. You may also see business case analysis examples.
Security Gap Analysis Table Template
Security Gap Analysis Template
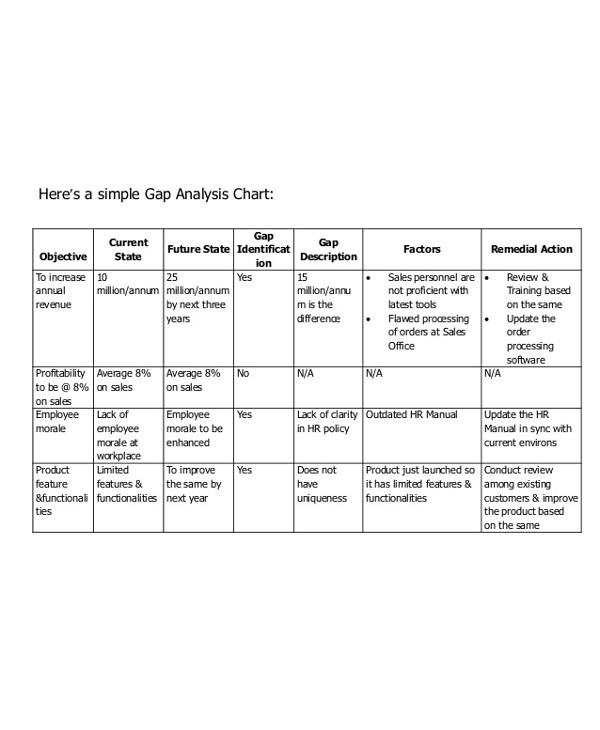
Simple Security Gap Analysis Chart
Developing an Information Security Program Gap Analysis
Developing and maintaining an information security program is a three-step process that is continually repeated and updated over time. The steps involved are measuring an existing program, identifying and implementing necessary improvements, and managing the ongoing process.You may also see quantitative analysis examples.
The first step, measuring where you are, can only be completed with the input of key managers who can articulate their understanding of the company’s strategic objectives, the current business environment, and expected industry changes and tactical issues, such as which security issues need immediate action and the effect that these issues may have on the business.
By linking strategic business goals with information security needs and identifying unique IT security challenges and opportunities, a framework can be established. In the next step, the gap between reality and desirability becomes more apparent, and a road map is developed to close the gap between them.
Assessing the information security is an opportunity to ask, and answer, tough questions like, “Does the organization have a formal strategic plan? If so, how well has it been working? Is its effectiveness even measurable? Has it been independently reviewed?
Since you can’t move forward into the process without first achieving a thorough understanding of the present condition of your information security, asking and knowing the answer to these questions is vital for you to proceed.
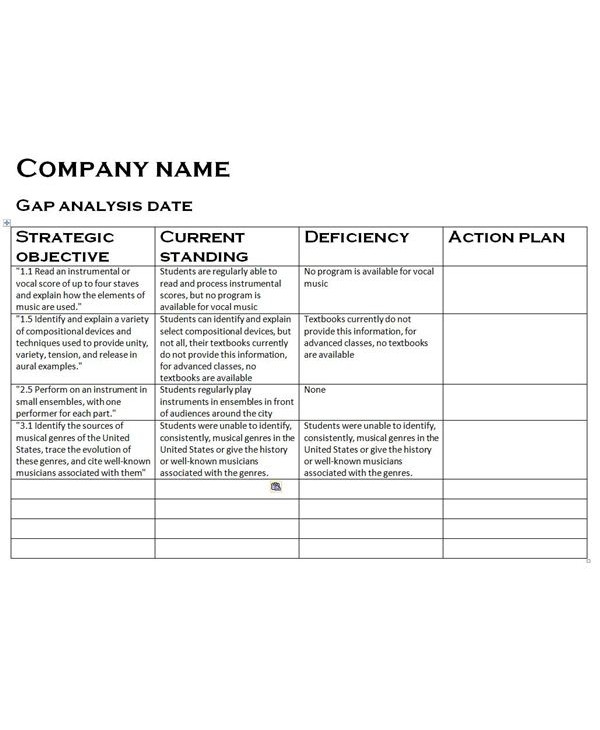
Although documenting the existing environment does not need to be detailed and exhaustive, it should at least provide a snapshot of the current state of the program, for you to be able to identify the aspects you need to address, especially those whose core components are your people, your operations, and your technology.Take a look at business systems analysis.
One of the most practical and reliable ways to gauge effectiveness is to compare your current program with your industry’s best practices. You can use them as scorecards to make it easier for you to grade your program in its key areas.
Once your existing program has been assessed, the organization must take a broad and unconstrained look at what an effective information security environment would look like. This picture will give them an idea, an inspiration, to the end product which they must work to achieve.You may also see education gap analysis examples.
The resulting security gap will highlight the difference between the current and future information security designs. In analyzing this gap, you should be able to separate strategic activities that ensure long-term success from more pressing tactical issues that require immediate attention. These gaps are then categorized into high, medium, and low priorities to make it easier to verify the relative importance of each.
This gap analysis provides the basis for the final step. With the results of the gap analysis in hand, an information security road map can be developed. The road map can help you address future funding issues using a return on investment approach, which can lead you to make easy investment decisions without sacrificing your much-needed security.Here are more free analysis examples.
Once you have determined the most appropriate investment level, you can start setting out strategic initiatives and tactical plans, along with a time frame for meeting those objectives. For best results, the road map should summarize program activities for the next two years.
When the road map is complete, you can start developing a much more detailed implementation plan that can log your progress toward each strategic initiative and its associated tactical plan. This project plan is also a valuable tool for reporting to management on the steady improvement in information security efforts.
Don’t forget that an information security program is a dynamic plan that must be regularly reviewed and revised. Constant corrections are needed. As new business challenges arise, information security must adapt. In fact, the program implementation process itself typically changes how a company conducts business. After all, the measures you’ve taken today may no longer be enough tomorrow.You may also see requirements analysis.
Achieving a completely secure company is not a realistic goal, although that is what we are all hoping for here. Unfortunately, security threats are too pervasive, not to mention unpredictable, and company networks too complex to be able to guarantee the confidentiality, integrity, and availability of all systems and information all the time.
But by continuously implementing incremental security measures that ultimately reduce risks, closing the security gap can become a business reality. It’s all about how hard you are willing to try to make it come true for you and your company.You may also see job analysis examples.
It’s easier for us to protect things we can actually see and touch. For example, our physical offices are teeming with security guards to make sure that no innocent stranger can come barging in to cause troubles. And if they do, we have security cameras providing us with footage of the crime scene so that the culprits can be recognized and caught.You may also see investment analysis examples.
If we go to such measures to protect our company, why can’t we extend the same level of precaution to another important aspect of our enterprise? We are now in a generation where computers are considered a necessity. They hold just as much important information as our physical location, and thus deserve just as much protection.You may also see customer analysis examples.
Unfortunately, the dangers that surround our computer data lurk behind screens too, which means that it’s almost impossible to identify, much less catch, them should they start playing with things that aren’t theirs. Knowing this vulnerability, the best thing we can do is to conduct a security gap analysis to make sure that our data is as protected as our office’s front doors.You may also see feasibility analysis examples.