Security Operational Plan
A security operational plan is one that encourages a management to view their operation through the perspective of an antagonist, to be able to objectively study their protective efforts and its adequacy in protecting the company’s sensitive information.
It is a type of risk management process that may include monitoring employee behaviors and habits, especially those that concern social media sites and sharing login credentials via professional emails or text messages. All of these are a combined attempt at trying to keep classified data from falling into the wrong hands.
Security Operational Plan Example
Security Management Develop Operational Plan Example
Building Security Operational Plan Example
The Job of Security Operation Plans
Have you ever had an object in your possession that you feel an extreme protectiveness for because other people seeing it would make you feel exposed? Perhaps it’s a journal, or a box of formal letters, or even your mobile phone where hundreds of private messages and pictures are stored. Whatever the case is, you try your best to keep these items from the hands of other people because their physical security is equal to your peace of mind.
The same unconscious rule goes for your business assets. You’ve spent money and time to own the piece of land on which your office has been built and the company name you can be proud of. Feeling the need to protect them is expected. After all, tangible assets also equate to measurable losses. You may also see operational plan for restaurant examples.
However, securing a site against physical, cyber, and human events can be staggering. There are so many things you have to do, and so many factors you are bound to miss, and so many risks you have to constantly keep a laundry list of.
But this has never stopped any sane management to keep fighting these risks, instead of simply waiting for them to strike, because trying to prevent them is always better, not to mention cheaper, than just waiting for the damage to be over so you can clean it. You may also like annual operational plan examples.
An operational security plan can help tackle different areas of security. Aside from the cyber and virtual aspects of your business, it will also encompass physical and personnel security, manufacturing system security, risk assessments, and procedural security.
Assets are both tangible and intangible, which means that the damage your company may suffer may or may not be visible to the naked eye.
Physical damages may be related to your site, equipment, or employee injury. Abstract damages may involve the loss of consumer and public trust and negative media image. Any of these two unique types of damages both have economic consequences to your company, which is why a quick response to them is vital. You may also check out event operational plan examples.
A security operational plan can give you the chance to mitigate risks by applying more levels of security on top of your existing ones, and reducing vulnerabilities by assessing defects in security and facilitating operations. It gives you a new chance of approaching security, one that involves your people, your general policies, and cyber and physical protection.
Physical Security Plan Example
Cyber Security and Physical Security Operational Plan
Hospital Emergency Operations Plan
The Five Steps Involved in Security Operational Plan
There are five steps involved in a basic security operational plan:
1. Identifying the company’s sensitive data.
To understand how much effort the company will have to exert in their security attempts, they must first identify which resources they will have to protect. This may include the facts and figures of their product research, their customer and employee information, their intellectual properties and assets, and their financial statements. Once the areas that need to be covered are itemized, specific efforts can then be designed to answer to these areas.
- Define your organization’s security objectives.
- Create standards that are relevant to your business field as your guidelines.
- Select the people who will be responsible for the implementation of your security plan.
2. Determine possible threats to the data.
As we’ve talked about earlier, a security operational plan prides itself in its ability to squarely assess its own company’s security exercises to study its existing deficiencies that outsiders may take advantage of. For every category of information that you believe to be sensitive (or those that we’ve previously identified), try to analyze what hazards are threatening the privacy of your data. You may also see hotel operational business plan examples.
Aside from third parties who may try to infiltrate and steal your information, it is also best to keep a constantly watchful eye for insider threats, such as negligent employees and unhappy workers who may be present in your own team. You may also like project operational plan examples.
- Perform a short threat analysis.
- Conduct an assessment of your current security’s vulnerabilities.
3. Inspect current security holes and other unanticipated vulnerabilities.
Assuming that the company already has current safeguards created as a protection from infiltrators, assess these attempts and look for possible weak and exposed areas that may be exploited, or that has already been trespassed without your knowledge, by external entities to gain access to your data. We are often too confident on our own efforts that we tend to oversee our security’s susceptibility to intruders. You may also see IT operational plan examples.
To truly gain a hundred percent assurance, try to constantly look at your security attempts as inadequate to continually encourage you and your team to work harder to strengthen it.
- Analyze the threats’ potential consequences.
- Rank the consequences and determine the vulnerabilities that must be reduced.
- Define the economic results of your mitigation efforts.
4. Calculate the amount of risk that is associated with each vulnerability.
Once you have discovered the existence of flaws in your security efforts, try to gauge how much trouble these weaknesses can cause you.
Judge each vulnerability using factors such as the likelihood of an actual attack happening, the degree of damage that the company will suffer, and the amount of effort and time that you will need to recuperate from the assault. If you’ve discovered which risk proves itself to be more pertinent and with higher chances of attack and more substantial damage, prioritize it during your mitigation efforts. You may also like hospital operational plan examples.
5. Prepare countermeasures.
Perhaps the most difficult part of the whole security operational planning process is preparing and implementing an antidote that can eliminate all the existent security threats and reduce the risks that they may cause.
Some of the pursuits you may take for this step is updating your hardware, creating new company policies regarding the protection of your sensitive data, and even training your employees on effective and healthy surveillance practices to help them understand the importance of their support in creating a company-wide security awareness.
- Identify the technical and procedural mitigation you may embrace.
- Implement them.
- Document the new policies and procedures you may have applied in relation to your attempts.
- Perform these general policies and turn them into a culture of security within your company.
Privacy Security Operation Plan Example
Emergency Security Operations Plan Example
Practices for Security Operations
The following are suggestions you may follow regarding the best practices that you can implement for a healthy security operational program
1. Implement exact change management processes.
If you’ve changed any company or network policy for security measures, update your employees about it so that they can perform according to the changes made. These updates must be logged and controlled so that they can be monitored, and their progress can be audited. You may also see primary school operational plan examples.
2. Restrict access to network devices.
Copy the rule of thumb that the military and many government entities have popularized. A “need to know” basis is applied regarding the access and sharing any kind of information, even within the company departments. This can keep outsiders, and those who do not have any use for the info, from being in contact with it. You may also like business plan examples.
3. Give minimum access even to your employees.
The most dangerous kind of information theft is infiltration, so to keep yourself from being completely sabotaged by your own team, only give them access to information that are necessary for them to perform their job. Avoid giving them other privileges such as admin access and financial records. You may also check out department strategic plan examples.
4. Implement dual control.
Avoid having the same set of people handling different jobs in your company. For example, a regular network employee should not be in charge of security to avoid any sort of abuse of power and access.
5. Rely on automating tasks to reduce your need for human intervention.
Due to technological advancements, this is no longer an impossible option for companies. If its possible for you to self-regulate tasks that may directly affect your company’s security, do so. Although humans are a company’s strongest asset, they are also its weakest security factor since people are prone to make mistakes, overlook details, and even forget things. You might be interested in hotel business plan examples.
6. Always have a robust disaster recovery plan.
Irregardless of how spotless your security operational plan is, you can’t simply rely on it to never fail you. You must always have a plan to identify new risks, steps on how to respond to them, and to reduce the possible damages they may cause. Only by doing so can you truly ensure your preparedness to answer to security issues. You may also see advertising and marketing business plan examples.
Security Operational Plan Management Control
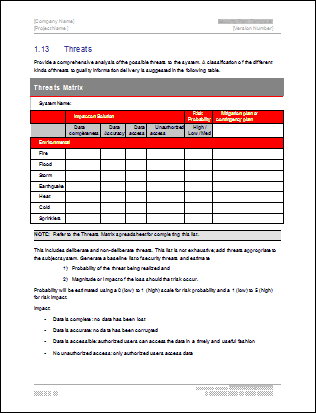
Security Operation Plan Threats Matrix
Conclusion
Promoting a culture of security in your everyday operations is cheaper than answering to the damages that a relaxed management may result in. Operational security is actually achievable. Yes, the road that can eventually lead to it is long and the processes extensive, but by taking small amounts of your time and effort into prevention can help ensure operational stability and continuity. You may also see personal plan examples.