10 SQL Injection Examples
SQL Injection is a web security vulnerability that allows attackers to interfere with the queries an application makes to its database. This flaw often occurs when user inputs are improperly sanitized, enabling malicious SQL statements to be executed. Exploiting SQL Injection can lead to unauthorized access, data breaches, and severe security risks. By manipulating input fields, such as HTML forms, attackers can inject malicious SQL code, compromising database integrity and exposing sensitive information. Proper input validation and parameterized queries are essential for prevention.
What is SQL Injection?
SQL Injection is a web security flaw where attackers inject malicious SQL code into input fields, manipulating database queries. This can lead to unauthorized access, data breaches, and compromised data integrity. Proper input validation and using parameterized queries help prevent SQL Injection attacks.
Simple SQL Injection Example
1. Basic SQL Injection: Suppose we have a login form where users enter their username and password:
— Normal Query
SELECT * FROM users WHERE username = ‘user’ AND password = ‘pass’;
— SQL Injection
SELECT * FROM users WHERE username = ‘user’ OR ‘1’=’1′ AND password = ‘pass’;
In this example, an attacker can input user' OR '1'='1 as the username. This modifies the query to always return true, potentially granting access without a valid password.
2. Bypassing Login: Another example where the attacker tries to bypass login:
— Normal Query
SELECT * FROM users WHERE username = ‘admin’ AND password = ‘password’;
— SQL Injection
SELECT * FROM users WHERE username = ‘admin’ — ‘ AND password = ”;
By inputting admin' -- as the username, the attacker comments out the rest of the query, effectively bypassing the password check.
3. Extracting Data: An example of extracting additional data using SQL Injection:
— Normal Query
SELECT * FROM users WHERE id = 1;
— SQL Injection
SELECT * FROM users WHERE id = 1; SELECT * FROM sensitive data;
Here, the attacker appends another SQL statement to extract data from a different table.
4. Using HTML Form: A vulnerable HTML form example:
<form action=”login.php” method=”post”>
Username: <input type=”text” name=”username”>
Password: <input type=”password” name=”password”>
<input type=”submit” value=”Login”> </form>
In login.php, an insecure query could be:
$username = $_POST[‘username’];
$password = $_POST[‘password’];
$query = “SELECT * FROM users WHERE username = ‘$username’ AND password = ‘$password'”;
An attacker can inject SQL code through the form inputs to manipulate the query.
5. Preventive Measure:
To prevent SQL Injection, use parameterized queries:
$stmt = $conn->prepare(“SELECT * FROM users WHERE username = ? AND password = ?”);
$stmt->bind_param(“ss”, $username, $password);
$stmt->execute();
This ensures user inputs are properly escaped and the query structure remains intact, preventing SQL Injection attacks.
Types of SQL Injection
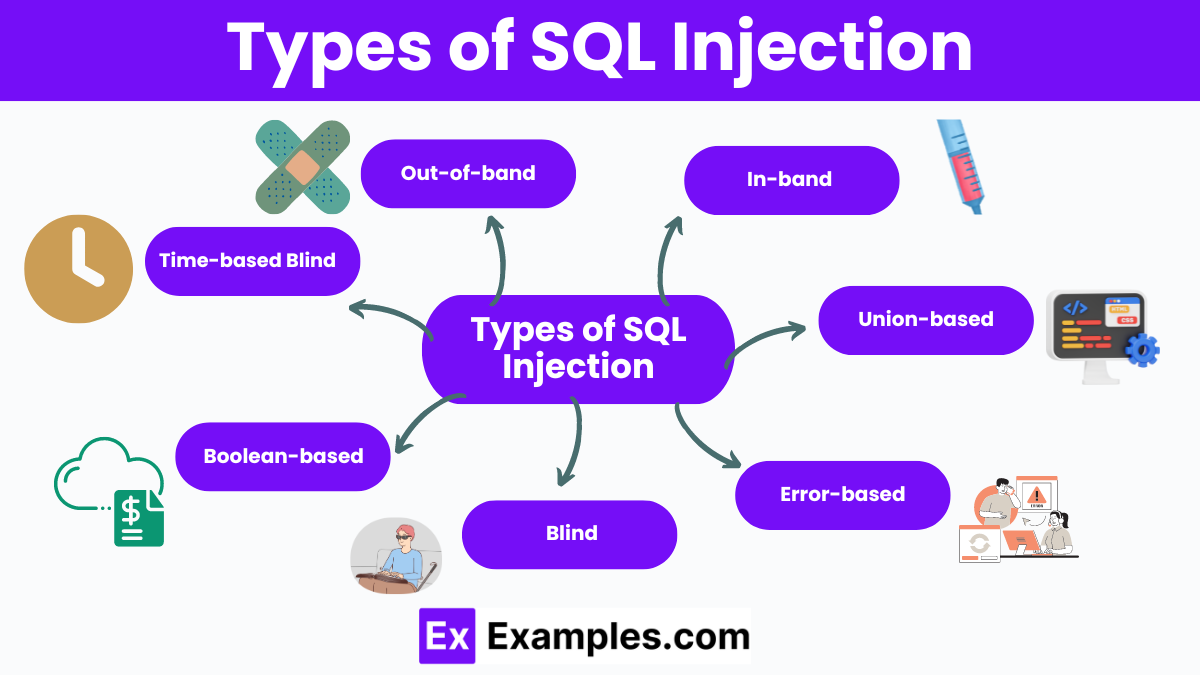
- In-band SQL Injection – Attacker uses the same communication channel to launch attacks and gather results, often through error messages.
- Union-based SQL Injection – Exploits the UNION SQL operator to combine results from multiple queries, retrieving hidden data.
- Error-based SQL Injection – Manipulates SQL queries to generate database error messages, revealing sensitive information.
- Blind SQL Injection – Attacker infers data based on true/false responses, as error messages are not displayed.
- Boolean-based Blind SQL Injection – Uses Boolean conditions to infer database information by observing different web responses.
- Time-based Blind SQL Injection – Attacker uses time delays to infer database information by measuring response times.
- Out-of-band SQL Injection – Utilizes different communication channels to retrieve data, often requiring specific database functionalities.
SQL Injection In Cyber Security
SQL Injection in cyber security is a critical vulnerability where attackers manipulate SQL queries to access unauthorized data. This technique can lead to data breaches, loss of data integrity, and significant security risks. Conducting a security risk assessment helps identify and mitigate such vulnerabilities, ensuring the protection of sensitive information and system integrity.
SQL Injection Prevention
SQL injection prevention involves using parameterized queries or prepared statements in SQL commands to separate data from commands, thereby preventing malicious SQL code execution. Input validation and avoiding dynamic SQL construction with user inputs also enhance security against SQL injection attacks.
How and Why Is an SQL Injection Attack Performed
An SQL injection attack is performed by injecting malicious SQL code into input fields of a vulnerable application, exploiting improper handling of user input. Attackers aim to bypass authentication, steal data, or modify databases, exploiting flaws like lack of input validation or improper SQL query construction.
How to detect SQL injection vulnerabilities
- Use web vulnerability scanners like Acunetix or Burp Suite.
- Employ manual testing with crafted inputs.
- Analyze server logs for suspicious queries.
SQL injection in different parts of the query
| Part of Query | Example |
|---|---|
| In a String | ' OR 1=1 -- |
| In a Numeric Value | 1; DROP TABLE users-- |
| In a WHERE clause | username = 'admin'--' AND password = 'password' |
SQL in Web Pages
- Database Interaction: Web pages use SQL queries to retrieve, insert, update, or delete data from databases like MySQL, PostgreSQL, etc.
- Dynamic Content: Queries are often embedded in server-side code (e.g., PHP, Python) to dynamically generate web content based on database data.
- Security Risks: Improperly handled SQL can lead to SQL injection attacks, where malicious SQL commands are injected via user inputs, compromising database security.
- Best Practices: Parameterized queries and ORM (Object-Relational Mapping) frameworks help mitigate risks by sanitizing inputs and separating SQL logic from user input.
SQL Injection Based on 1=1 is Always True
SQL Injection: Exploiting 1=1 Condition
- Vulnerability Exploitation
SQL queries not sanitized allow attackers to inject malicious SQL code. - Understanding 1=1 Condition
Injecting ‘1=1’ in WHERE clause makes the condition true for all rows. - Consequences of Exploitation
Enables unauthorized access, data leakage, or manipulation of database content.
SQL Injection Test
- Input Manipulation: Inserting special characters (‘ or 1=1 –) into input fields to see if the application responds unexpectedly or allows unauthorized access.
- Error Messages: Provoking error messages by inputting unexpected data formats or characters to see if SQL error messages disclose database structure or sensitive information.
- Union Queries: Attempting to append additional queries using UNION operators to retrieve data from other tables.
- Time Delays: Inserting sleep or wait commands to see if the application delays its response, indicating potential successful injection.
- Authentication Bypass: Trying to bypass login forms by injecting SQL queries that could authenticate without valid credentials.
How does SQL injection work?
Attackers inject malicious SQL code into input fields of an application.
What can SQL injection exploit?
It can exploit vulnerabilities in SQL queries to gain unauthorized access or manipulate data.
Why is SQL injection dangerous?
It can lead to data loss, unauthorized access, or complete server compromise.
How can SQL injection be prevented?
By using parameterized queries or prepared statements.
What are common signs of SQL injection?
Unexpected results, slow application response, or error messages revealing SQL code.
Can SQL injection affect any database?
Yes, any database driven by SQL can be vulnerable.
How can developers protect against SQL injection?
By validating and sanitizing input data and using ORM frameworks.
What role does input validation play?
It ensures that data entered into an application is within acceptable parameters.
What is parameterized querying?
It involves using placeholders for parameters in SQL statements.
Are web applications the only targets for SQL injection?
No, any application that uses SQL queries is potentially vulnerable.
10 SQL Injection Examples
SQL Injection is a web security vulnerability that allows attackers to interfere with the queries an application makes to its database. This flaw often occurs when user inputs are improperly sanitized, enabling malicious SQL statements to be executed. Exploiting SQL Injection can lead to unauthorized access, data breaches, and severe security risks. By manipulating input fields, such as HTML forms, attackers can inject malicious SQL code, compromising database integrity and exposing sensitive information. Proper input validation and parameterized queries are essential for prevention.
What is SQL Injection?
SQL Injection is a web security flaw where attackers inject malicious SQL code into input fields, manipulating database queries. This can lead to unauthorized access, data breaches, and compromised data integrity. Proper input validation and using parameterized queries help prevent SQL Injection attacks.
Simple SQL Injection Example
1. Basic SQL Injection: Suppose we have a login form where users enter their username and password:
— Normal Query
SELECT * FROM users WHERE username = ‘user’ AND password = ‘pass’;
— SQL Injection
SELECT * FROM users WHERE username = ‘user’ OR ‘1’=’1′ AND password = ‘pass’;
In this example, an attacker can input user' OR '1'='1 as the username. This modifies the query to always return true, potentially granting access without a valid password.
2. Bypassing Login: Another example where the attacker tries to bypass login:
— Normal Query
SELECT * FROM users WHERE username = ‘admin’ AND password = ‘password’;
— SQL Injection
SELECT * FROM users WHERE username = ‘admin’ — ‘ AND password = ”;
By inputting admin' -- as the username, the attacker comments out the rest of the query, effectively bypassing the password check.
3. Extracting Data: An example of extracting additional data using SQL Injection:
— Normal Query
SELECT * FROM users WHERE id = 1;
— SQL Injection
SELECT * FROM users WHERE id = 1; SELECT * FROM sensitive data;
Here, the attacker appends another SQL statement to extract data from a different table.
4. Using HTML Form: A vulnerable HTML form example:
<form action=”login.php” method=”post”>
Username: <input type=”text” name=”username”>
Password: <input type=”password” name=”password”>
<input type=”submit” value=”Login”> </form>
In login.php, an insecure query could be:
$username = $_POST[‘username’];
$password = $_POST[‘password’];
$query = “SELECT * FROM users WHERE username = ‘$username’ AND password = ‘$password'”;
An attacker can inject SQL code through the form inputs to manipulate the query.
5. Preventive Measure:
To prevent SQL Injection, use parameterized queries:
$stmt = $conn->prepare(“SELECT * FROM users WHERE username = ? AND password = ?”);
$stmt->bind_param(“ss”, $username, $password);
$stmt->execute();
This ensures user inputs are properly escaped and the query structure remains intact, preventing SQL Injection attacks.
Types of SQL Injection

In-band SQL Injection – Attacker uses the same communication channel to launch attacks and gather results, often through error messages.
Union-based SQL Injection – Exploits the UNION SQL operator to combine results from multiple queries, retrieving hidden data.
Error-based SQL Injection – Manipulates SQL queries to generate database error messages, revealing sensitive information.
Blind SQL Injection – Attacker infers data based on true/false responses, as error messages are not displayed.
Boolean-based Blind SQL Injection – Uses Boolean conditions to infer database information by observing different web responses.
Time-based Blind SQL Injection – Attacker uses time delays to infer database information by measuring response times.
Out-of-band SQL Injection – Utilizes different communication channels to retrieve data, often requiring specific database functionalities.
SQL Injection In Cyber Security
SQL Injection in cyber security is a critical vulnerability where attackers manipulate SQL queries to access unauthorized data. This technique can lead to data breaches, loss of data integrity, and significant security risks. Conducting a security risk assessment helps identify and mitigate such vulnerabilities, ensuring the protection of sensitive information and system integrity.
SQL Injection Prevention
SQL injection prevention involves using parameterized queries or prepared statements in SQL commands to separate data from commands, thereby preventing malicious SQL code execution. Input validation and avoiding dynamic SQL construction with user inputs also enhance security against SQL injection attacks.
How and Why Is an SQL Injection Attack Performed
An SQL injection attack is performed by injecting malicious SQL code into input fields of a vulnerable application, exploiting improper handling of user input. Attackers aim to bypass authentication, steal data, or modify databases, exploiting flaws like lack of input validation or improper SQL query construction.
How to detect SQL injection vulnerabilities
Use web vulnerability scanners like Acunetix or Burp Suite.
Employ manual testing with crafted inputs.
Analyze server logs for suspicious queries.
SQL injection in different parts of the query
Part of Query | Example |
|---|---|
In a String |
|
In a Numeric Value |
|
In a WHERE clause |
|
SQL in Web Pages
Database Interaction: Web pages use SQL queries to retrieve, insert, update, or delete data from databases like MySQL, PostgreSQL, etc.
Dynamic Content: Queries are often embedded in server-side code (e.g., PHP, Python) to dynamically generate web content based on database data.
Security Risks: Improperly handled SQL can lead to SQL injection attacks, where malicious SQL commands are injected via user inputs, compromising database security.
Best Practices: Parameterized queries and ORM (Object-Relational Mapping) frameworks help mitigate risks by sanitizing inputs and separating SQL logic from user input.
SQL Injection Based on 1=1 is Always True
SQL Injection: Exploiting 1=1 Condition
Vulnerability Exploitation
SQL queries not sanitized allow attackers to inject malicious SQL code.Understanding 1=1 Condition
Injecting ‘1=1’ in WHERE clause makes the condition true for all rows.Consequences of Exploitation
Enables unauthorized access, data leakage, or manipulation of database content.
SQL Injection Test
Input Manipulation: Inserting special characters (‘ or 1=1 –) into input fields to see if the application responds unexpectedly or allows unauthorized access.
Error Messages: Provoking error messages by inputting unexpected data formats or characters to see if SQL error messages disclose database structure or sensitive information.
Union Queries: Attempting to append additional queries using UNION operators to retrieve data from other tables.
Time Delays: Inserting sleep or wait commands to see if the application delays its response, indicating potential successful injection.
Authentication Bypass: Trying to bypass login forms by injecting SQL queries that could authenticate without valid credentials.
How does SQL injection work?
Attackers inject malicious SQL code into input fields of an application.
What can SQL injection exploit?
It can exploit vulnerabilities in SQL queries to gain unauthorized access or manipulate data.
Why is SQL injection dangerous?
It can lead to data loss, unauthorized access, or complete server compromise.
How can SQL injection be prevented?
By using parameterized queries or prepared statements.
What are common signs of SQL injection?
Unexpected results, slow application response, or error messages revealing SQL code.
Can SQL injection affect any database?
Yes, any database driven by SQL can be vulnerable.
How can developers protect against SQL injection?
By validating and sanitizing input data and using ORM frameworks.
What role does input validation play?
It ensures that data entered into an application is within acceptable parameters.
What is parameterized querying?
It involves using placeholders for parameters in SQL statements.
Are web applications the only targets for SQL injection?
No, any application that uses SQL queries is potentially vulnerable.

