Preparing for the CIA Exam requires a thorough understanding of “Fraud Risks,” a fundamental aspect of the auditing profession. Mastery of fraud risk identification, assessment, and mitigation strategies is essential. This knowledge helps in safeguarding organizational assets and ensuring financial integrity, crucial for excelling in the CIA Exam.
Learning Objective
In studying “Fraud Risks” for the CIA Exam, you should aim to understand the concepts and methodologies used to identify, assess, and mitigate fraud within organizations. Analyze different types of fraud risks, such as asset misappropriation, corruption, and financial statement fraud. Evaluate the principles behind effective fraud detection techniques like data analytics, forensic analysis, and whistleblower systems. Additionally, explore how these methods are implemented in real-world auditing scenarios to prevent and detect fraud. Apply your knowledge to evaluate case studies and design audit procedures that effectively address fraud risks in preparation for the CIA Exam.
Introduction to Fraud Risks
Fraud risks refer to the potential for individuals or organizations to engage in deceptive practices intended to gain unauthorized benefits, such as financial gain or competitive advantages. Understanding and managing fraud risks is crucial for maintaining the integrity, financial stability, and reputation of any organization. Here’s an introduction to the concept of fraud risks, highlighting key aspects:
Nature of Fraud Risks
Fraud risks can arise from various sources both internal and external to an organization. These risks often involve:
- Asset Misappropriation: Theft or misuse of an organization’s resources.
- Corruption: Offering or accepting bribes or kickbacks, and engaging in business dealings that are illegal or unethical.
- Financial Statement Fraud: Manipulation of financial records to present a false picture of a company’s financial health, often to meet financial targets or manipulate stock prices.
Common Factors Contributing to Fraud Risks
Several factors can increase the likelihood of fraud within an organization, including:
- Inadequate Internal Controls: Weaknesses in financial and operational controls can create opportunities for fraud.
- Complexity and Ambiguity: Complex structures or ambiguous policies that can be easily manipulated or misunderstood.
- Incentives and Pressures: Financial pressures on employees or management to meet unrealistic performance goals.
- Rationalization: A cultural or ethical climate that makes it easier for perpetrators to justify their fraudulent actions.
Identifying and Assessing Fraud Risks
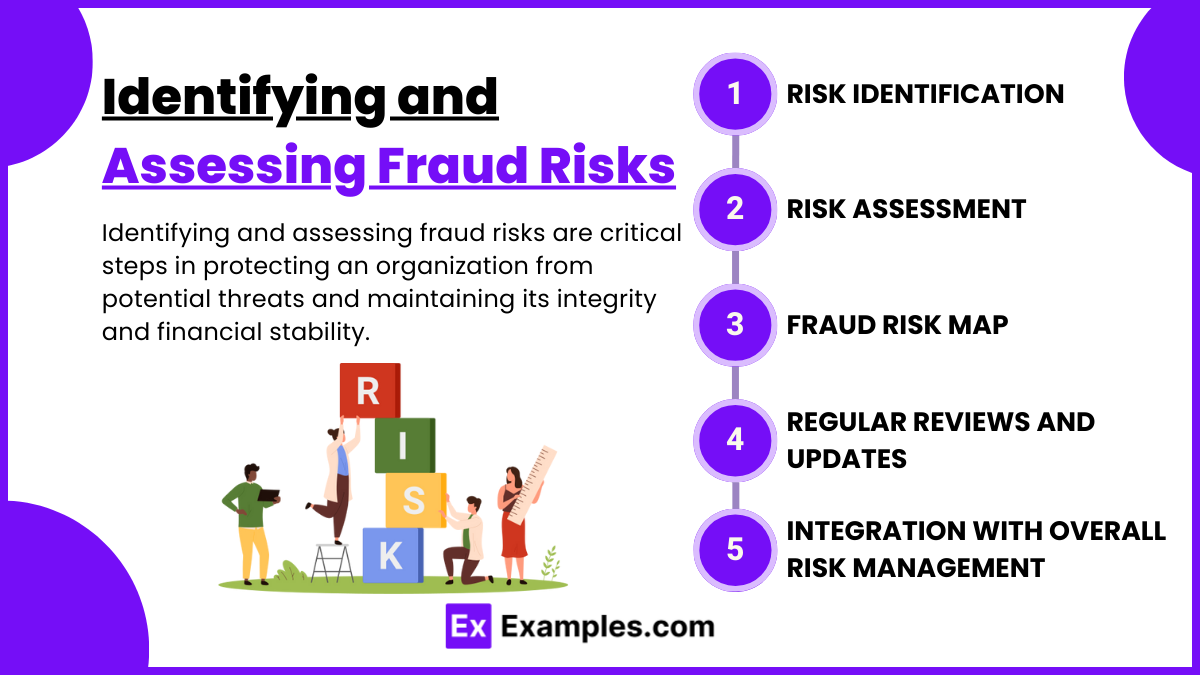
Identifying and assessing fraud risks are critical steps in protecting an organization from potential threats and maintaining its integrity and financial stability. Here’s how organizations can effectively identify and assess fraud risks:
1. Risk Identification
- Analyze Business Processes: Identify vulnerable areas within business operations like procurement or sales.
- Gather Insights: Use surveys or interviews with employees across all levels to uncover potential vulnerabilities.
- Industry Benchmarking: Learn from common fraud issues within the industry and peer experiences.
2. Risk Assessment
- Risk Scoring: Assign scores to each identified risk based on likelihood and impact, prioritizing them accordingly.
- Scenario Analysis: Develop scenarios to explore possible fraud occurrences and involved parties.
- Historical Review: Examine past fraud incidents to spot patterns and weaknesses.
3. Fraud Risk Map
- Visualization: Combine identification and assessment data to map fraud risks, showing their probability and potential effects.
4. Regular Reviews and Updates
- Dynamic Update: Regularly revisit and update fraud risk assessments to adapt to organizational changes and external shifts.
5. Integration with Overall Risk Management
- Strategic Alignment: Ensure fraud risk management is incorporated within the broader risk management framework to align strategies and resources.
Fraud Detection Techniques
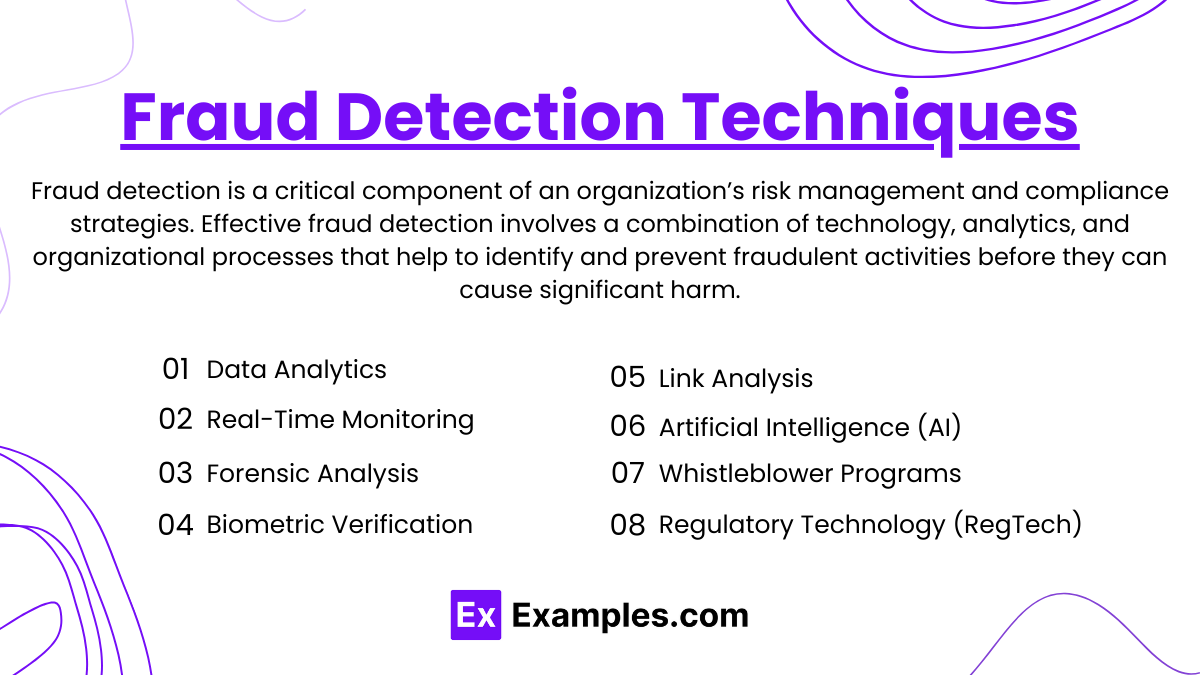
Fraud detection is a critical component of an organization’s risk management and compliance strategies. Effective fraud detection involves a combination of technology, analytics, and organizational processes that help to identify and prevent fraudulent activities before they can cause significant harm. Here are some key techniques used in fraud detection:
1. Data Analytics
- Statistical Analysis: Uses statistical techniques to identify anomalies in data that deviate from normal patterns.
- Predictive Modeling: Leverages historical data to build models that predict the likelihood of fraudulent transactions.
- Machine Learning: Employs algorithms that can learn from and make decisions based on data, improving over time as they are exposed to more transactions.
2. Real-Time Monitoring
- Transaction Monitoring: Continuous surveillance of transactions to flag unusual activities based on pre-defined criteria such as unusually high amounts or transactions at odd times.
- Account Monitoring: Tracks user account behavior to detect anomalies, such as irregular login patterns or unusual changes in personal information.
3. Forensic Analysis
- Digital Forensics: Involves the recovery and investigation of material found in digital devices, often used after fraud has been detected to understand the methods and gather evidence.
- Auditing: Regular and ad-hoc audits can uncover discrepancies in financial records that may indicate fraudulent activities.
4. Biometric Verification
- Identity Checks: Uses biometric data, like fingerprints or facial recognition, to verify if the person conducting the transaction is the legitimate account holder.
5. Link Analysis
- Social Network Analysis: Examines relationships between individuals, accounts, and devices to find hidden connections and patterns associated with fraudulent schemes.
6. Artificial Intelligence (AI)
- Natural Language Processing (NLP): AI techniques analyze communications and documentation for signs of fraud or deceptive language.
- Anomaly Detection: AI systems are trained to continuously learn from data transactions, flagging those that are out of the ordinary.
7. Whistleblower Programs
- Internal Reporting Systems: Encourages employees, vendors, and customers to report suspected fraud anonymously, often leading to early detection.
8. Regulatory Technology (RegTech)
- Compliance Tools: Specialized software that helps companies comply with regulations and monitor for fraudulent activities by streamlining data collection and analysis.
Case Studies and Real-World Applications
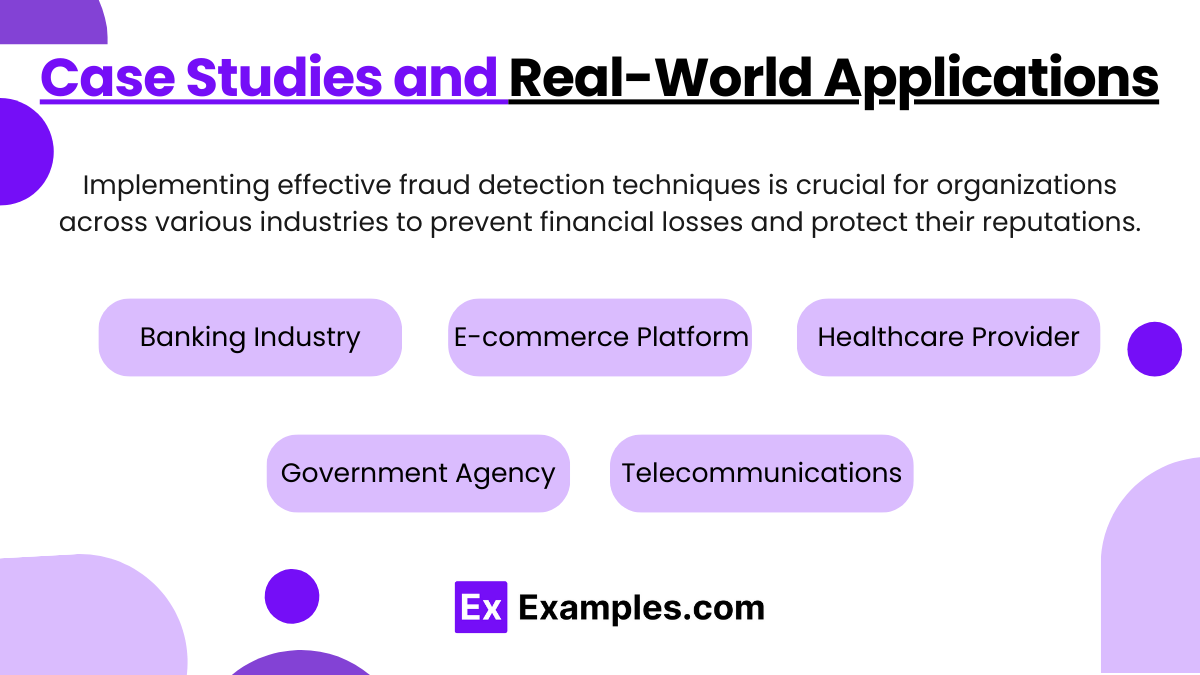
Implementing effective fraud detection techniques is crucial for organizations across various industries to prevent financial losses and protect their reputations. Here are several case studies demonstrating how different fraud detection techniques have been successfully applied in real-world scenarios:
Case Study 1: Banking Industry
- Issue: Credit card fraud.
- Solution: Implementation of machine learning models for real-time transaction analysis.
- Outcome: Significant reduction in fraudulent transactions and faster response times.
Case Study 2: E-commerce Platform
- Issue: High rate of return fraud.
- Solution: Data analytics used to track and analyze return patterns and customer behavior.
- Outcome: Reduced return fraud and improved customer service for legitimate returns.
Case Study 3: Healthcare Provider
- Issue: Insurance claim fraud.
- Solution: AI and link analysis to monitor claims and detect irregularities.
- Outcome: Identification of fraudulent claims before processing, reducing financial losses.
Case Study 4: Government Agency
- Issue: Tax evasion.
- Solution: AI-driven anomaly detection systems to analyze tax returns.
- Outcome: Recovery of substantial amounts of evaded taxes and deterrence of future fraud.
Case Study 5: Telecommunications Company
- Issue: Subscription fraud.
- Solution: Real-time monitoring and biometric verification during account creation.
- Outcome: Drastic reduction in subscription fraud and enhanced customer trust.
Examples
Example 1: Asset Misappropriation
- This is the most common form of fraud, where employees steal or misuse the organization’s resources. Examples include theft of cash, falsifying expense reports, or using company property for personal gain.
Example 2: Corruption
- Corruption involves unethical behavior by employees, often in positions of power, who use their status to obtain personal benefits. Common forms include bribery (offering something of value to influence a decision), kickbacks (receiving unauthorized benefits in exchange for favorable treatment), and conflicts of interest (acting against the organization’s best interests for personal gain).
Example 3: Financial Statement Fraud
- This involves intentional misrepresentation of financial information to mislead stakeholders about an organization’s financial health. Techniques may include revenue recognition schemes, concealing liabilities, or artificially inflating assets.
Example 4: Payroll Fraud
- In payroll fraud, employees or payroll staff manipulate the payroll system to issue payments based on false claims. This can include ghost employees (payrolls processed for non-existent workers), unauthorized bonuses, or inflated wages.
Example 5: Procurement Fraud
- Procurement fraud occurs in the purchasing of goods and services and can include bid rigging (manipulating the bidding process to ensure a particular vendor wins), submitting false invoices, or purchasing personal items using company funds.
Practice Questions
Question 1
Which of the following is an example of asset misappropriation?
A. Inflating sales figures on financial statements
B. Accepting bribes from a supplier
C. Stealing office supplies from work
D. Overstating travel expenses
Answer: C. Stealing office supplies from work
Explanation:
Asset misappropriation involves the theft or misuse of an organization’s assets. Stealing office supplies fits directly under this category as it represents the theft of physical assets from the company. Overstating travel expenses (D) also involves asset misappropriation but relates specifically to expense fraud. In contrast, inflating sales figures (A) is an example of financial statement fraud, and accepting bribes (B) falls under corruption.
Question 2
What is a primary motivation behind financial statement fraud?
A. To gain a personal advantage from workplace resources
B. To influence the stock price or meet financial targets
C. To seek revenge against the company
D. To reduce personal workload
Answer: B. To influence the stock price or meet financial targets
Explanation:
Financial statement fraud is typically committed by company management to influence the stock price or to meet financial benchmarks set by external stakeholders. This type of fraud is aimed at creating a false impression of the company’s financial health to maintain investor confidence or meet regulatory criteria. The other options do not directly relate to the motivations for financial statement fraud.
Question 3
Which of the following controls is most effective in preventing payroll fraud?
A. Regular job rotations and mandatory vacations
B. Installing surveillance cameras in the finance department
C. Conducting external audits annually
D. Providing ethical training to employees
Answer: A. Regular job rotations and mandatory vacations
Explanation:
Regular job rotations and mandatory vacations are effective internal controls that prevent payroll fraud by reducing the opportunity for any single employee to perpetrate and conceal fraudulent activities over an extended period. These practices help expose fraudulent activities that might go unnoticed if employees never change their roles or take breaks from their duties. Surveillance cameras (B) and ethical training (D) may help but are less directly effective in addressing the specific risks associated with payroll fraud. External audits (C) are also beneficial but are more about detection than prevention.


