Preparing for the CIA Exam requires a thorough understanding of “Information Technology,” a vital aspect in the field of internal auditing. This area emphasizes the effective management of technological resources and the protection of IT infrastructure against risks such as unauthorized access, data breaches, and system failures. It involves identifying and mitigating potential IT vulnerabilities, ensuring adherence to technology policies, and upholding best practices in system management. Developing expertise in IT enables auditors to assess the robustness of an organization’s IT framework, recommend system improvements, and safeguard digital assets with precision. Strengthening IT knowledge is crucial for promoting system reliability, enhancing operational efficiency, and achieving success on the CIA Exam.
Learning Objectives
In studying “Information Technology” for the CIA exam, you should learn the core components of IT, including systems, applications, and networks that manage data processing, storage, and communication. Key areas to learn include IT governance frameworks like COBIT and ITIL, which guide the alignment of IT with business goals, risk management, and compliance. Learn about essential processes such as change management, access control, and incident response to maintain system security and reliability. IT audits are important to learn for assessing controls, identifying vulnerabilities, and ensuring data integrity, system reliability, and privacy. This knowledge supports the secure and efficient use of IT resources within the organization.
Introduction of Information Technology

Information Technology (IT) has become an integral component of internal auditing, significantly transforming how audits are conducted. The integration of IT into auditing practices enhances the auditor’s ability to conduct thorough examinations of financial records and operational processes. With sophisticated tools and techniques, IT enables auditors to streamline their workflows, improve data analysis, and achieve higher levels of efficiency and effectiveness in their work. This transformation is not just about adopting new technologies; it reflects a fundamental shift in the role of internal auditors, who must now navigate a complex technological landscape while maintaining their core responsibilities of ensuring accuracy and compliance.
Role of Information Technology
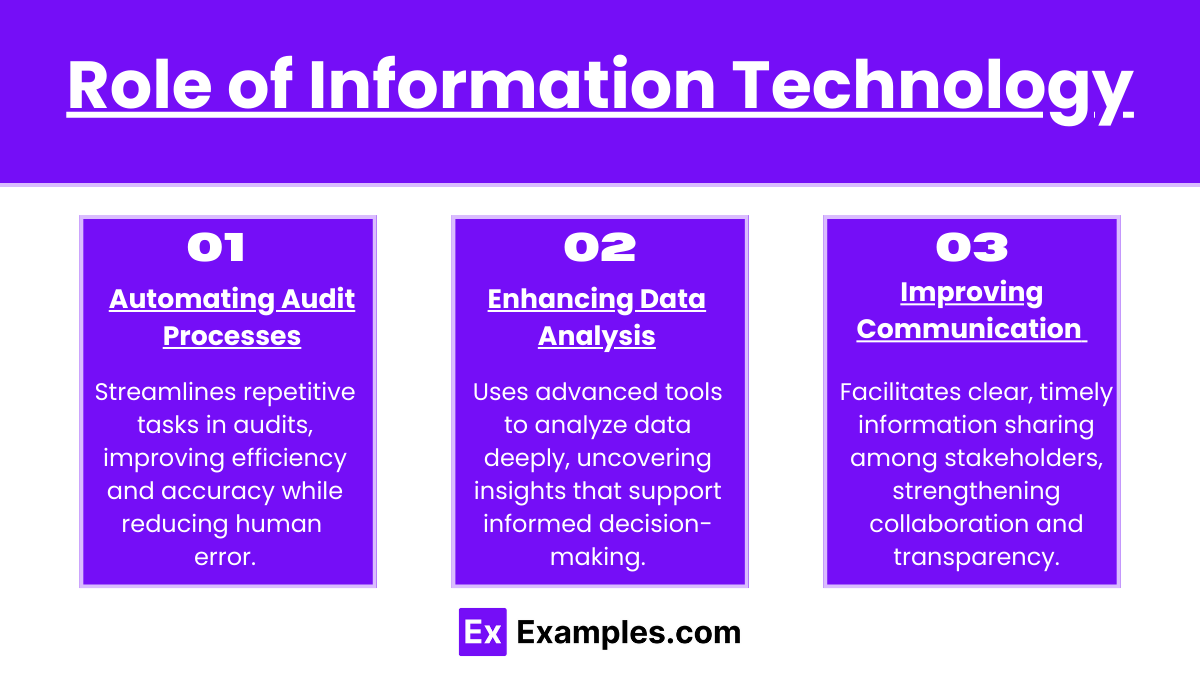
The primary role of IT in internal auditing encompasses several critical areas:
1. Automating Audit Processes
One of the most significant contributions of IT to internal auditing is the automation of routine audit tasks. Traditional auditing often involves manual processes that can be time-consuming and prone to error. By leveraging IT systems, auditors can automate these repetitive tasks, which not only reduces the manual effort required but also increases overall productivity. Automation tools can handle functions such as data collection, reconciliation, and reporting, freeing auditors to focus on more strategic activities that add value to the organization.
2. Enhancing Data Analysis
In the age of big data, the ability to analyze vast amounts of information quickly and accurately is paramount. IT tools, such as data analytics software, empower auditors to conduct complex analyses of large datasets. These tools can identify trends, detect anomalies, and reveal insights that might go unnoticed with traditional audit methods. For instance, auditors can apply statistical methods to assess risks and pinpoint areas requiring improvement, enabling more proactive risk management.
3. Improving Communication
Effective communication is essential in auditing, and information technology plays a pivotal role in facilitating this. IT enables better communication among audit team members and stakeholders through various collaboration tools. Features such as document sharing, real-time updates, and messaging applications enhance teamwork and ensure that everyone involved in the audit process is aligned and informed. This improved collaboration helps to streamline workflows and reduce the potential for miscommunication.
Key IT Tools in Auditing
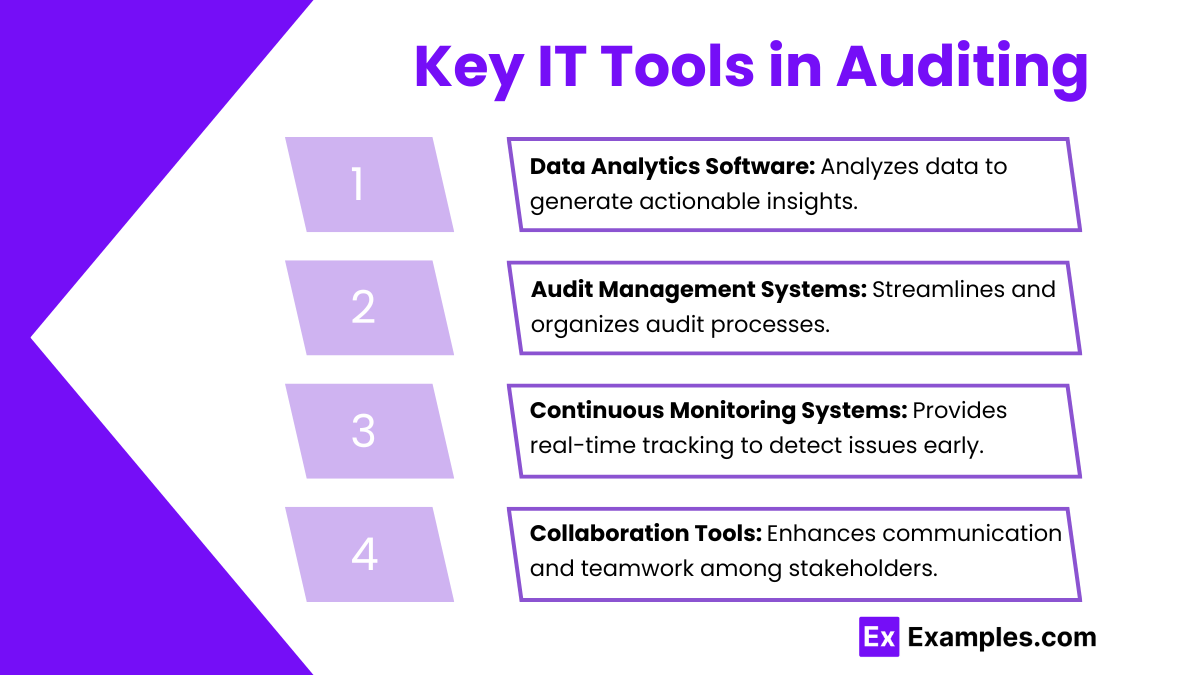
Several key IT tools are crucial for enhancing the efficiency and effectiveness of audits:
1. Data Analytics Software
Tools like Tableau, ACL, and IDEA are at the forefront of data analytics in auditing. These applications allow auditors to perform complex data analyses that help uncover insights which might be missed using conventional audit methods. By visualizing data and employing advanced statistical techniques, auditors can identify patterns and anomalies, thereby facilitating informed decision-making.
2. Audit Management Systems
Platforms such as TeamMate and AuditBoard are designed to manage the entire audit lifecycle, from planning through execution and reporting. These systems provide a centralized repository for all audit-related documentation, making it easier to track progress, manage tasks, and ensure compliance with established protocols. This systematic approach reduces administrative burdens and enhances overall audit efficiency.
3. Continuous Monitoring Systems
Continuous monitoring systems provide ongoing oversight of financial transactions, enabling auditors to detect unusual activities in real time. This proactive approach to auditing allows for immediate intervention in cases of potential fraud or compliance violations. Continuous monitoring systems help organizations stay ahead of risks, ensuring that corrective actions can be implemented swiftly.
4. Collaboration Tools
Technologies like Microsoft Teams and Slack enhance communication and collaboration among audit teams. These platforms facilitate document sharing and discussions, allowing auditors to collaborate more effectively, regardless of their physical location. By promoting a culture of teamwork and open communication, collaboration tools contribute to the overall success of the audit process.
Benefits of Using Information Technology
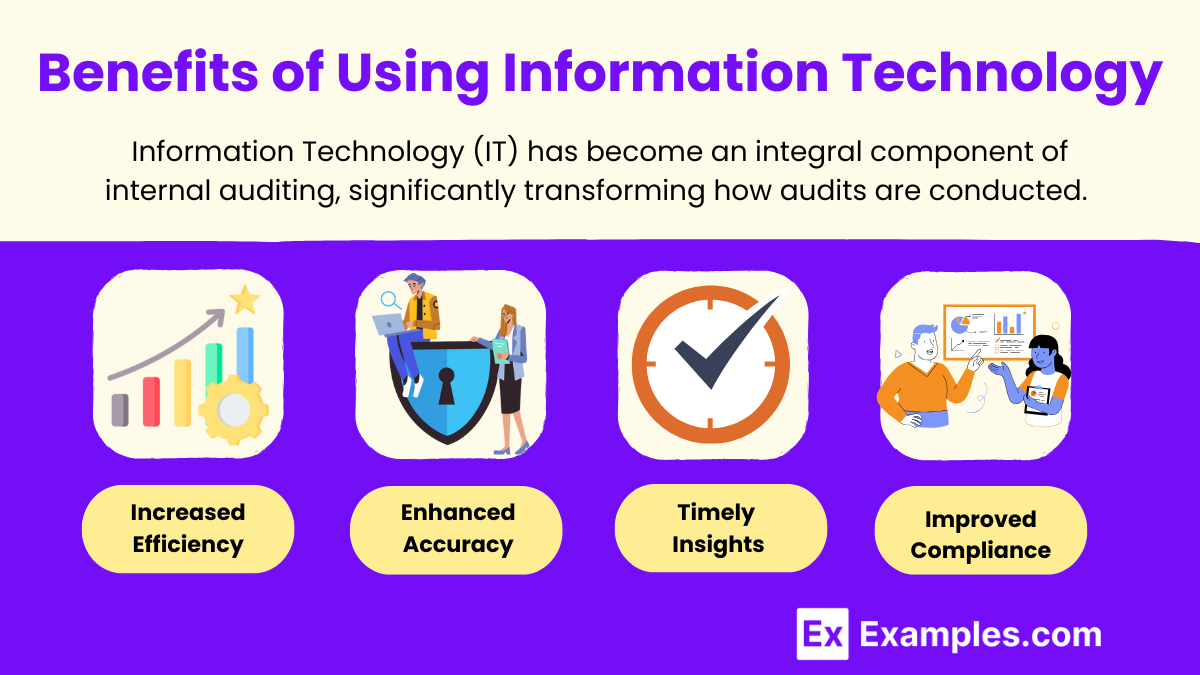
The incorporation of IT into auditing yields several notable benefits:
1. Increased Efficiency
The automation of repetitive tasks and the use of advanced analytics streamline audit processes. This increased efficiency allows auditors to allocate more time to high-value tasks, such as strategic planning and risk assessment, rather than being bogged down by manual data entry or basic analysis. As a result, organizations can complete audits more quickly and effectively.
2. Enhanced Accuracy
IT tools significantly reduce the risk of human error in data collection and analysis, leading to more reliable audit outcomes. With automated processes, the likelihood of mistakes diminishes, allowing auditors to produce precise reports and analyses. Enhanced accuracy not only builds trust in the audit results but also supports better decision-making by management.
3. Timely Insights
Access to real-time data empowers auditors to make informed decisions promptly. When auditors can view and analyze data as it is generated, they can respond to issues as they arise, rather than waiting for periodic reviews. This agility is critical in today’s fast-paced business environment, where timely insights can significantly impact organizational performance.
4. Improved Compliance
IT facilitates adherence to regulatory standards and internal policies by providing tools for documentation and monitoring. Automated systems can track compliance activities, ensuring that all necessary protocols are followed. By maintaining robust compliance frameworks, organizations can mitigate risks and avoid costly penalties associated with non-compliance.
Challenges of Implementing IT in Auditing
Despite its many advantages, the implementation of IT in auditing does come with challenges:
1. Cybersecurity Risks
The increased reliance on technology exposes organizations to cybersecurity threats. Sensitive financial data is often targeted by malicious actors, necessitating robust security measures to protect this information. Auditors must be vigilant in assessing cybersecurity risks and implementing appropriate safeguards to protect organizational data.
2. Integration Issues
Integrating new IT systems with existing processes and technologies can pose significant challenges. Organizations may face compatibility issues, requiring substantial time and resources to address. Successful integration is critical to ensuring that auditors can leverage new tools effectively without disrupting ongoing audit activities.
3. Training Needs
As technology evolves, auditors must continuously update their skills to keep pace with new tools and methodologies. Training programs are essential to ensure that audit professionals are proficient in utilizing IT systems effectively. Without adequate training, auditors may struggle to maximize the benefits of IT, ultimately hindering the overall audit process.
Examples
Example 1. Enhancing Communication
Information technology has transformed communication within organizations. Tools such as email, instant messaging, and video conferencing platforms enable employees to connect in real time, regardless of their physical location. This not only speeds up the decision-making process but also fosters collaboration across departments and geographical boundaries. With the ability to share documents and information instantly, teams can work more efficiently, resulting in improved productivity and streamlined workflows.
Example 2. Streamlining Business Processes
Companies increasingly utilize information technology to automate routine tasks and streamline business processes. For instance, enterprise resource planning (ERP) systems integrate various functions like finance, human resources, and supply chain management into a single platform. This consolidation helps in reducing redundancies, minimizing errors, and enhancing operational efficiency. By leveraging technology, organizations can optimize their operations, ultimately leading to cost savings and better resource allocation.
Example 3. Improving Data Management
Information technology plays a crucial role in data management and analysis. Businesses can collect vast amounts of data from various sources, including customer interactions, sales figures, and market trends. Advanced data analytics tools enable organizations to analyze this data to uncover insights and inform strategic decisions. With better data management practices, companies can enhance their forecasting accuracy, improve customer targeting, and identify opportunities for growth.
Example 4. Facilitating E-Commerce
The rise of information technology has revolutionized the retail landscape, enabling businesses to engage in e-commerce. Through online platforms, companies can reach a global audience, allowing customers to browse and purchase products from the comfort of their homes. Payment gateways, inventory management systems, and customer relationship management (CRM) tools further enhance the online shopping experience, ensuring secure transactions and personalized customer service. As a result, businesses can increase their sales and expand their market presence.
Example 5. Strengthening Cybersecurity Measures
As organizations rely more on information technology, the importance of cybersecurity has become paramount. Companies implement various IT security measures to protect sensitive data and maintain customer trust. Firewalls, encryption, and intrusion detection systems are essential tools used to safeguard networks from unauthorized access and cyber threats. By investing in robust cybersecurity protocols, businesses can mitigate risks and ensure the integrity of their operations in an increasingly digital world.
Practice Questions
Question 1
What does the term “cloud computing” refer to?
A) The use of physical servers located on-premises.
B) The delivery of computing services over the internet.
C) The installation of software applications directly on user devices.
D) The process of upgrading computer hardware.
Correct Answer: B) The delivery of computing services over the internet.
Explanation:
Cloud computing involves providing various services—such as storage, processing power, and applications—over the internet instead of through local servers or personal devices. This model allows users to access and utilize technology resources without direct management or maintenance of the infrastructure. It enhances scalability, flexibility, and collaboration, making it an essential aspect of modern IT environments.
Question 2
Which of the following best describes “phishing”?
A) A technique used to improve network security.
B) An attack method that involves misleading individuals to disclose personal information.
C) A process for encrypting sensitive data.
D) A strategy for optimizing website performance.
Correct Answer: B) An attack method that involves misleading individuals to disclose personal information.
Explanation:
Phishing is a type of cyber attack that typically involves fraudulent emails or messages that appear to be from reputable sources. The attackers aim to deceive individuals into providing sensitive information, such as usernames, passwords, or credit card numbers. This information is then used for malicious purposes, including identity theft and financial fraud. Recognizing phishing attempts is crucial for maintaining personal and organizational security.
Question 3
What is the primary purpose of a firewall in network security?
A) To store backup copies of important data.
B) To manage user access to network resources.
C) To filter incoming and outgoing network traffic based on predetermined security rules.
D) To provide antivirus protection for computers.
Correct Answer: C) To filter incoming and outgoing network traffic based on predetermined security rules.
Explanation:
A firewall acts as a security barrier between a trusted internal network and untrusted external networks, such as the internet. It monitors and controls network traffic based on predefined rules, allowing or blocking data packets accordingly. Firewalls can help prevent unauthorized access to or from a private network, making them a fundamental component of cybersecurity strategies. They do not handle data storage, user access management, or antivirus protection directly but work alongside these systems to provide comprehensive security.