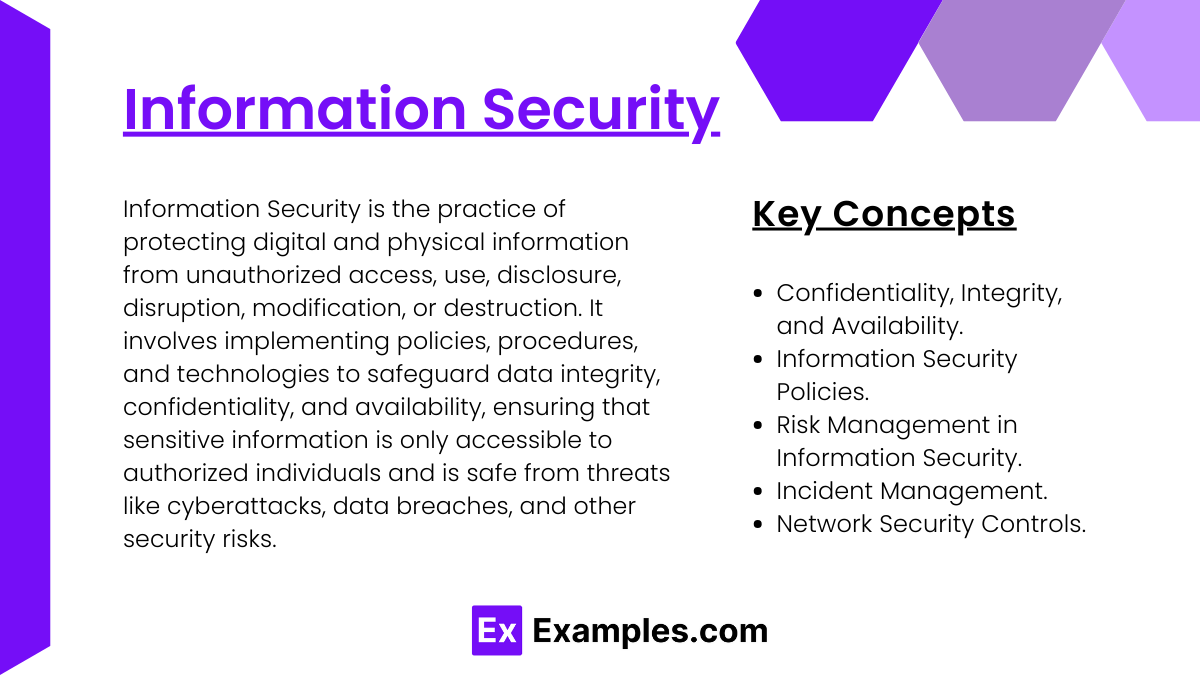
Preparing for the CIA Exam requires a robust understanding of “Information Security,” a critical element in internal auditing. This area focuses on safeguarding organizational data and ensuring information systems are secure against unauthorized access, breaches, and other cybersecurity threats. It involves recognizing potential vulnerabilities, implementing preventive controls, and assessing compliance with security policies and regulations. Mastering information security skills equips auditors with the knowledge to evaluate risk management strategies, recommend security enhancements, and protect sensitive information effectively. Strengthening information security knowledge is essential for maintaining data integrity, fostering trust, and achieving success on the CIA Exam.
Learning Objectives
In studying “Information Security” for the CIA exam, you should learn about the critical processes and controls that protect an organization’s information assets from various security risks. Information security is built on the CIA triad: Confidentiality, Integrity, and Availability. Confidentiality involves safeguarding sensitive information by restricting access to authorized individuals through methods like access controls, encryption, and data classification. Integrity focuses on maintaining the accuracy and consistency of data, ensuring it is not altered in unauthorized ways.Techniques such as checksums, version control, and access logging are key to preserving data integrity.Availability ensures that information and systems are accessible to authorized users when needed, supported by measures like redundancy, backup solutions, and disaster recovery planning.
Key Concepts in Information Security
- Confidentiality, Integrity, and Availability (CIA Triad):
- Confidentiality involves ensuring that sensitive information is only accessible to authorized personnel. Measures like encryption, user access controls, and secure communication channels help uphold confidentiality.
- Integrity ensures that data remains accurate, consistent, and unaltered except by authorized activities. Methods to maintain integrity include checksums, hash functions, and stringent data management processes.
- Availability guarantees that authorized users can access information when needed. Redundancies, system backups, and disaster recovery plans are essential for maintaining availability.
- Information Security Policies:
- Governance Frameworks (e.g., ISO 27001) provide structures for managing InfoSec across an organization. Policies developed within these frameworks outline roles, responsibilities, acceptable use, and response protocols.
- Access Control Policies define rules to ensure users have access only to the information necessary for their roles. Access can be controlled by systems like Role-Based Access Control (RBAC) or Mandatory Access Control (MAC), following the principle of least privilege.
- Risk Management in Information Security:
- Risk Assessment is the process of identifying, analyzing, and evaluating risks to information systems. It involves understanding potential threats, vulnerabilities, and the potential impact of security breaches.
- Risk Mitigation strategies are the actions taken to reduce risks to acceptable levels. Common methods include installing firewalls, implementing intrusion prevention systems (IPS), and establishing incident response plans.
- Incident Management:
- Incident Response Plan (IRP): This is a structured approach to handle the aftermath of a security incident, including detection, analysis, containment, eradication, and recovery.
- Forensic Analysis: In the event of a security breach, forensic techniques help investigate the incident by analyzing digital footprints, logs, and data patterns to identify the source and scope of the breach.
- Network Security Controls:
- Firewalls: These act as barriers between trusted internal networks and untrusted external networks, filtering incoming and outgoing traffic based on established rules.
- Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS): IDS monitors network or system activities for malicious actions or policy violations, while IPS actively prevents these actions.
Purposes of Information Security
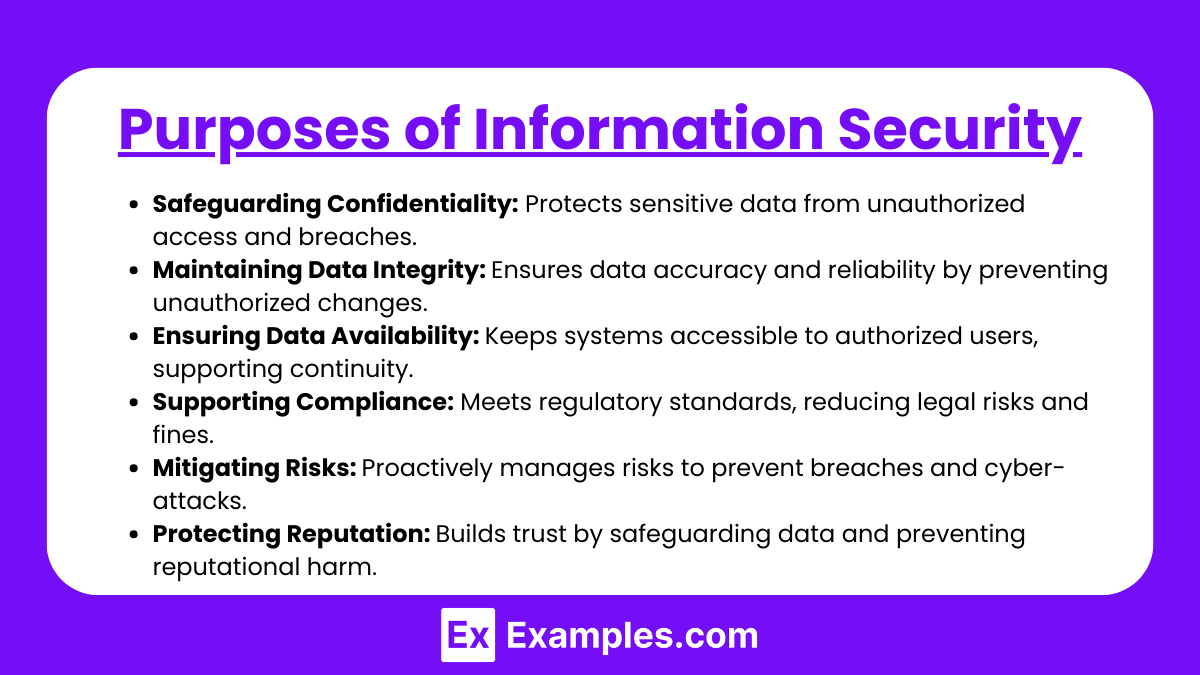
- Safeguarding Confidentiality:
- Ensures that sensitive data, such as personal information, financial details, and intellectual property, remains accessible only to authorized users. Confidentiality safeguards protect against data leaks, unauthorized access, and breaches.
- Maintaining Data Integrity:
- Preserves the accuracy and consistency of data throughout its lifecycle, preventing unauthorized alterations. Integrity ensures that information remains trustworthy and reliable, which is crucial for decision-making and regulatory compliance.
- Ensuring Data Availability:
- Guarantees that information and systems are accessible to authorized users when needed. Availability supports business continuity, minimizes downtime, and ensures that essential processes are not interrupted due to security incidents or system failures.
- Supporting Compliance and Legal Requirements:
- Helps organizations meet regulatory standards (e.g., GDPR, HIPAA, SOX) that mandate specific InfoSec controls for handling sensitive data. By ensuring compliance, InfoSec reduces the risk of legal repercussions and fines.
- Mitigating Risks and Reducing Threat Exposure:
- Identifies, assesses, and mitigates risks associated with information systems and data. This proactive approach reduces the likelihood of breaches, cyber-attacks, and data loss, ensuring a safer operational environment.
- Protecting Organizational Reputation:
- Prevents the negative impact on brand image and customer trust that can result from data breaches. Effective InfoSec practices build public and stakeholder confidence, demonstrating that the organization values and protects its information assets.
Types of Information Security Controls
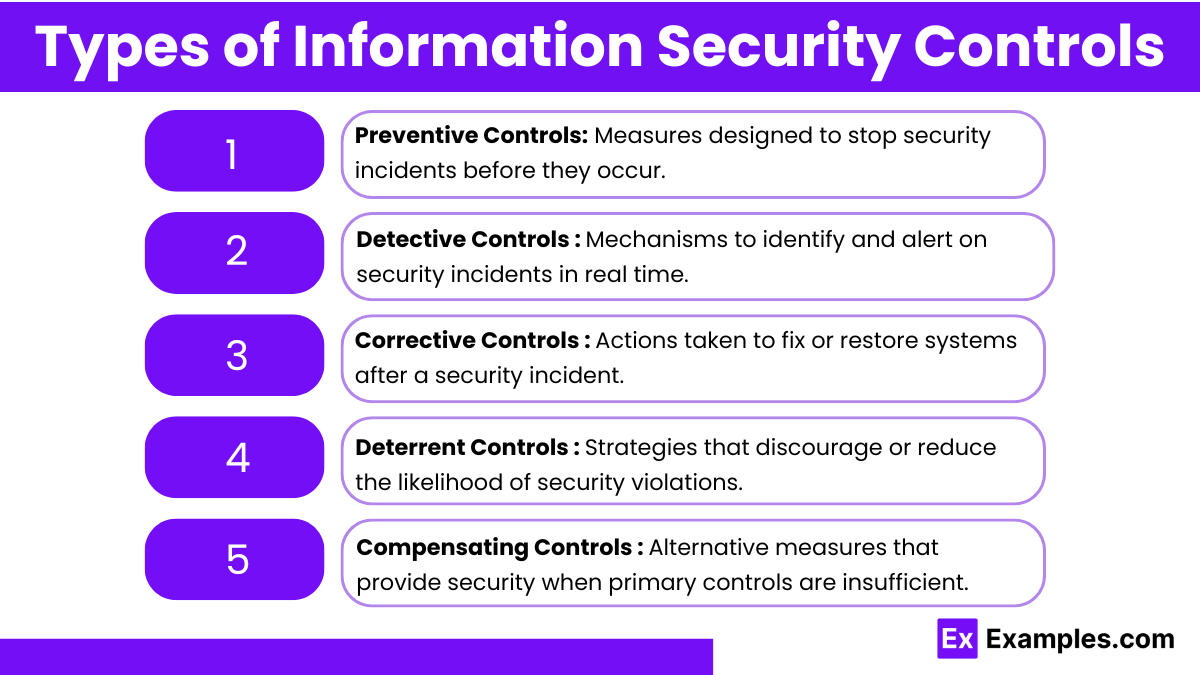
1. Preventive Controls
Preventive controls are designed to proactively deter and prevent security incidents before they can happen. These controls focus on establishing protocols, technologies, and behaviors that reduce the likelihood of unauthorized access, alterations, or data breaches. By implementing preventive measures, organizations aim to stop harmful activities before they occur, ensuring that sensitive information remains protected. Preventive controls are typically implemented at various levels of an organization’s infrastructure, including network, application, and physical layers, where they act as the first line of defense. They create barriers or conditions that make unauthorized actions more challenging or less feasible, thereby reducing the risk of potential threats.
2. Detective Controls
Detective controls aim to identify and notify security teams about incidents during or after they happen. Unlike preventive controls, detective measures focus on recognizing signs of unauthorized activity, data breaches, or security policy violations. These controls don’t stop incidents from occurring but instead provide visibility into unusual or suspicious activities, enabling rapid detection and response. They often involve systems that continuously monitor and analyze security data to identify potential incidents in real-time or shortly after they occur. This type of control is crucial in helping security teams understand the scope and details of an event, allowing them to take appropriate steps to contain and assess the impact of a security incident.
3. Corrective Controls
Corrective controls are essential for responding to detected incidents and addressing any damage or impact that has occurred. These controls are designed to minimize the consequences of a security event and to restore systems, data, and applications to their original, secure state. Corrective measures often involve procedures and tools that repair, modify, or adjust systems to ensure that operations can resume with minimal disruption. They aim to contain the incident, remediate the vulnerability, and prevent a recurrence. By promptly addressing issues post-detection, corrective controls limit the impact on business continuity and ensure that affected systems are promptly returned to a safe and stable condition.
4. Deterrent Controls
Deterrent controls serve to discourage malicious actors from attempting unauthorized activities by presenting risks or negative consequences. These controls function as psychological barriers, warning potential offenders about the repercussions of their actions, which may include detection and legal or disciplinary action. By establishing a visible presence of security measures or policies, deterrent controls create an environment that feels less accessible to attackers. These controls may involve communication strategies that let individuals know about the presence of strong security measures, making them think twice about engaging in harmful behavior. They play a vital role in reinforcing the organization’s stance on security and emphasizing the vigilance of monitoring efforts.
5. Compensating Controls
Compensating controls are alternative measures that are put in place to address and reduce risk when a primary control is either unavailable, not feasible, or insufficient to fully meet security requirements. These controls act as secondary security mechanisms that support or replace primary controls in circumstances where limitations exist. For instance, when an organization cannot implement a specific preventive measure due to resource constraints or technical challenges, a compensating control can serve to mitigate the associated risk. They are tailored to meet specific organizational needs and are carefully selected based on their ability to provide an acceptable level of security. By implementing compensating controls, organizations ensure continuous protection and compliance even when the ideal solution is out of reach.
Examples
Example 1. Implementing Data Encryption for Secure Communication
Organizations use information security to safeguard communication channels by implementing encryption protocols. This process ensures that sensitive data, like financial transactions or personal information, is transmitted securely over networks. Encryption converts the original data into a coded format, which can only be accessed by authorized personnel with decryption keys. For instance, when an employee accesses company data remotely, encryption protects it from interception by unauthorized users, bolstering confidentiality and trust within the digital communication infrastructure.
Example 2. Establishing Access Control Mechanisms
Information security strategies prioritize access control to regulate who can view or modify critical data within an organization. By implementing user authentication systems, such as multi-factor authentication (MFA) and role-based access control (RBAC), companies ensure that only authorized individuals have access to sensitive information. For instance, only upper management may be granted access to high-level financial data, while specific employees are permitted to access client information. This level of control mitigates unauthorized access risks, which can lead to data breaches and regulatory penalties.
Example 3. Utilizing Security Audits to Identify Vulnerabilities
Regular security audits are integral to using information security effectively within an organization. By conducting periodic assessments of digital infrastructure, organizations can identify and address potential vulnerabilities that malicious actors could exploit. For example, a security audit may reveal outdated software in the company’s database management system, which could expose the organization to data breaches. By addressing these weaknesses promptly, companies can enhance their resilience against cyber threats and maintain a secure operational environment.
Example 4. Applying Data Loss Prevention (DLP) Strategies
Information security incorporates data loss prevention techniques to ensure sensitive information remains within secure boundaries and is not shared inadvertently or maliciously. DLP tools monitor and control data transfer across devices and networks, preventing unauthorized access or data leakage. For example, a financial institution might use DLP software to restrict employees from transferring client data to unapproved devices or platforms, thereby reducing the risk of data breaches and ensuring compliance with industry regulations.
Example 5. Ensuring Compliance with Regulatory Standards
Information security also involves adhering to industry-specific compliance standards that mandate data protection protocols. Standards such as GDPR (General Data Protection Regulation) or HIPAA (Health Insurance Portability and Accountability Act) outline specific requirements for handling personal or health-related data. For instance, a healthcare provider may implement policies for securely storing and managing patient records to comply with HIPAA standards, ensuring that sensitive information remains confidential and that the organization avoids costly penalties for non-compliance.
Practice Questions
Question 1
Which of the following is NOT a component of the CIA Triad in Information Security?
A) Confidentiality
B) Integrity
C) Authentication
D) Availability
Answer: C) Authentication
Explanation:
The CIA Triad is a fundamental model in information security, representing three core principles: Confidentiality, Integrity, and Availability.
- Confidentiality ensures that sensitive information is accessed only by authorized individuals.
- Integrity means maintaining the accuracy and completeness of data.
- Availability ensures that information and resources are accessible to authorized users when needed.
Authentication is a separate concept and, while crucial for security (ensuring that the user is who they claim to be), it is not part of the CIA Triad. Thus, the correct answer is C.
Question 2
Which of the following measures is primarily focused on ensuring data confidentiality?
A) Implementing a firewall to block unauthorized access
B) Regularly backing up data to secure storage
C) Using hashing algorithms to verify data integrity
D) Conducting periodic audits to check for compliance
Answer: A) Implementing a firewall to block unauthorized access
Explanation:
Confidentiality in information security is about protecting data from unauthorized access. A firewall is a security measure that restricts network traffic, allowing only authorized data and users to access certain systems.
- Option A (Implementing a firewall) is directly aimed at controlling access, thereby supporting confidentiality.
- Option B (Backing up data) is focused on data availability, not confidentiality.
- Option C (Using hashing algorithms) is mainly used for data integrity, ensuring data hasn’t been altered.
- Option D (Periodic audits) is a compliance and control measure, not directly tied to confidentiality.
Question 3
What is the main purpose of a hashing algorithm in information security?
A) Encrypting data to keep it secure
B) Verifying data integrity by detecting changes
C) Storing data in an unrecognizable format
D) Creating passwords for user accounts
Answer: B) Verifying data integrity by detecting changes
Explanation:
A hashing algorithm is a cryptographic function that transforms data into a fixed-size hash value, which is unique to the data’s contents. If the data changes, the hash value changes, making hashing a common technique for verifying data integrity.
- Option A (Encrypting data) is incorrect because encryption protects data confidentiality, whereas hashing is not intended for encryption.
- Option C (Storing data in an unrecognizable format) is also incorrect, as hashing doesn’t store data but represents it with a unique identifier.
- Option D (Creating passwords) is not the purpose of hashing; however, hash functions are often used to store password hashes securely.


